In the contemporary landscape where digital security is paramount, we at HackenProof constantly strive to uphold our commitment towards our clients’ privacy and transparency. Today, we are excited to announce the implementation of end-to-end reports encryption on our bug bounty platform.
Decoding End-to-End Encryption
End-to-end encryption is a system that safeguards data to prevent unauthorized access or modification by third parties. This security protocol is designed to ensure that only you and the person you’re communicating with can read what is sent and nobody else, not even HackenProof.
The process is quite straightforward – the reports are encrypted by the sender (in this case, the hackers) and then decrypted by the recipient (the company members) locally on their device. Despite the reports passing through various channels such as cloud storage providers or other intermediaries that transmit or store the data, it remains encrypted. These intermediaries handle the data as per their normal procedures, yet they cannot decrypt and access the information.
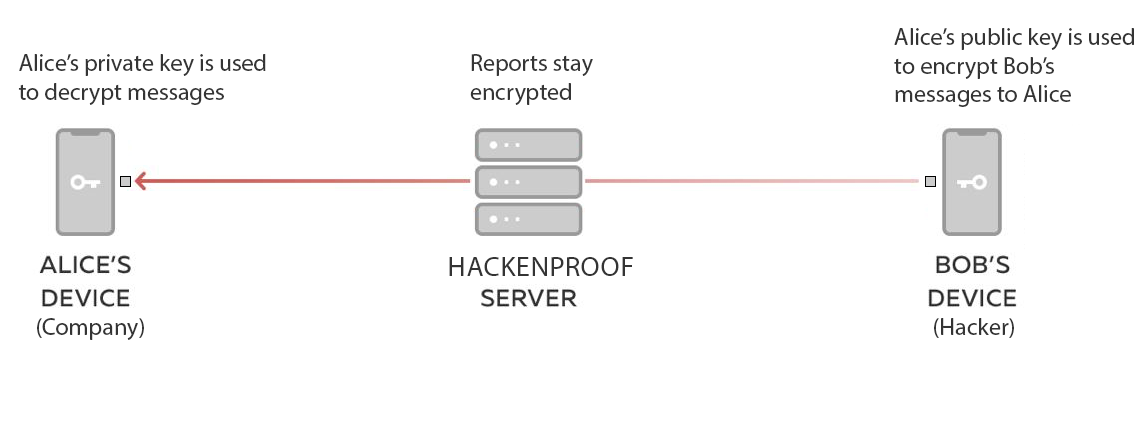
Understanding End-to-End Encryption on HackenProof
Implementing end-to-end encryption on HackenProof is a simple process, yet it provides a strong layer of security.
To initiate reports encryption, a company first generates its own PGP keypair, which consists of a public key and a private key. This public key is then provided to our team at HackenProof.
Once we receive the public key, we enable report encryption for the company and display a label indicating that encryption is in use. This visibility reassures hackers about the additional security measures in place.
For hackers, the process remains unchanged. They submit a report as they always would, specifying data & files which are then encrypted on their end before it goes to our backend.
The company then retrieves the encrypted data and decrypts it locally using their private key, thereby ensuring a secure, private information exchange.
What Can Be Encrypted On HackenProof?
At HackenProof, our end-to-end encryption service extends to a broad range of data, encompassing text and multiple file formats. These include bmp, gif, jpeg, png, pdf, mpeg, mp4, mov, csv, txt, zip, sol, rs, md, ts and more.
With this new feature, we aim to bolster our stance on secure, transparent data exchange while strengthening our clients’ trust.
Want to know any further questions or clarifications? Get in touch to request a demo with our team today!

