How it works
In a new era of financial services, decentralized finances (DeFi) allowed users to access lending and borrowing functionalities without intermediaries. A flash loan is a unique feature in DeFi that allows users to borrow a substantial amount of cryptocurrency without the need for collateral. The borrowed funds must be repaid within the same transaction block, making flash loans appealing for executing complex financial maneuvers, such as arbitrage, collateral swapping, and market manipulation.
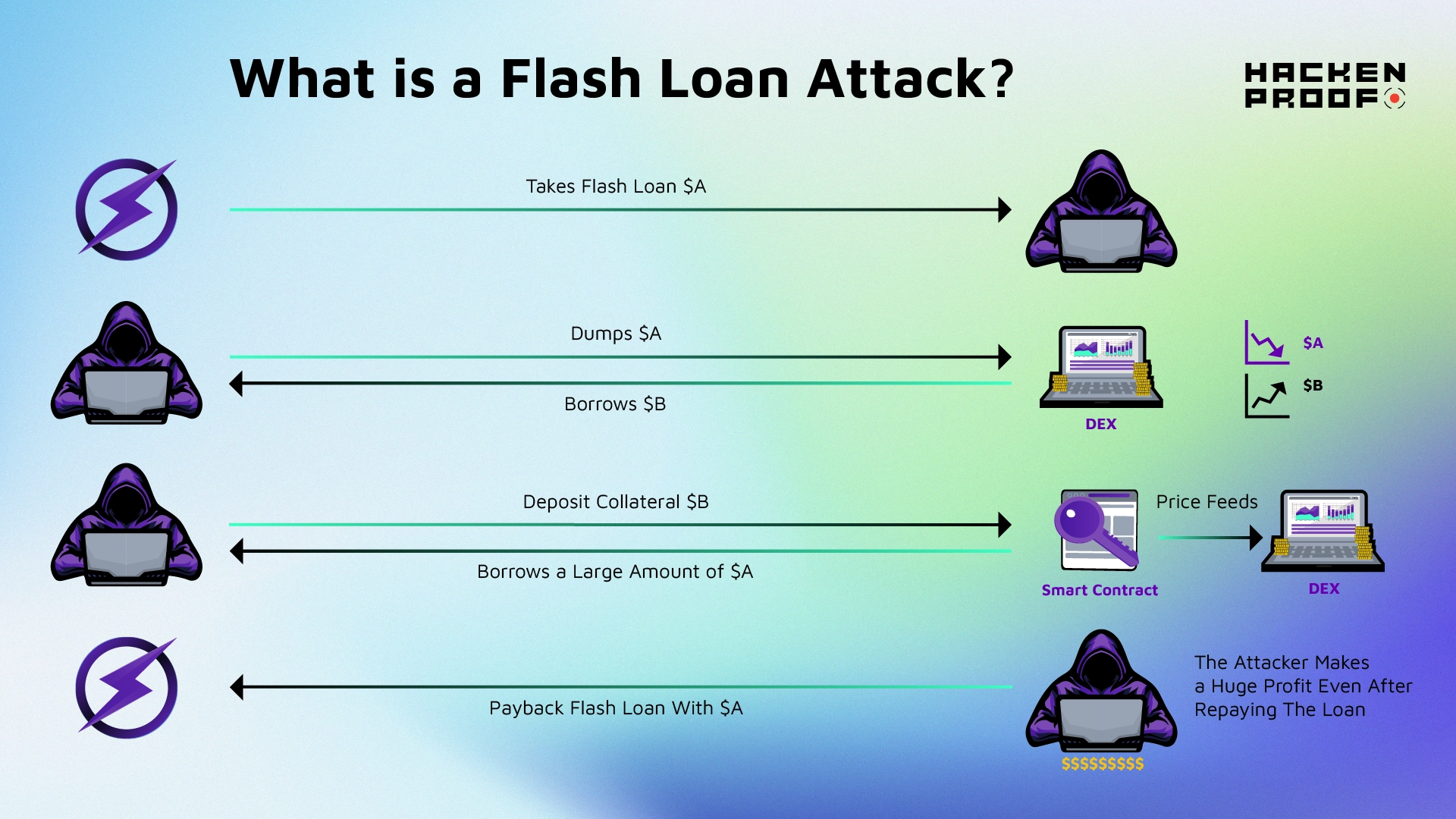
Flash loan attacks exploit the instantaneous borrowing and repayment mechanism of flash loans to manipulate markets and generate illicit profits. The algorithm behind a flash loan attack typically follows these steps:
Step 1: Borrowing the Flash Loan
The attacker initiates a flash loan request from a lending protocol, borrowing a significant amount of cryptocurrency, usually in stablecoins. The transaction for borrowing and repaying the loan must be executed within the same block.
Step 2: Executing the Attack
With the borrowed funds, the attacker executes a series of precisely timed transactions across various DeFi platforms. The specific attack strategies are different, but they often consist of one of the following types:
a. Price Manipulation: The attacker targets an asset with low liquidity on a DEX and artificially affects its price. This lures unsuspecting traders into buying or selling at manipulated prices, enabling the attacker to profit from the price disparity.
b. Arbitrage Opportunities: The attacker identifies price discrepancies across multiple platforms and exploits them for risk-free arbitrage. By simultaneously buying and selling assets at different prices, the attacker generates profits without providing any collateral.
c. Collateral Manipulation: The attacker triggers a series of liquidations on a DeFi lending platform by causing sudden price fluctuations in a highly collateralized asset. This results in forced liquidations and potential buying opportunities for the attacker.
Step 3: Repayment and Profits
After executing the attack successfully, the attacker repays the entire flash loan and a nominal fee to the lending platform. The profits gained from the manipulated transactions remain with the attacker, leaving the targeted DeFi platforms and users to bear the losses.
Real-world cases
On April 17, 2022, Beanstalk Farm experienced a loss of $182 million, propelling it to the forefront of crypto platforms targeted by flash loan exploits. Functioning as a stablecoin protocol on the Ethereum network, its recently deployed governance mechanism, known as “Curve LP Silos,” was compromised.
Leveraging the power of flash loans, the perpetrator gained significant voting authority within the system. Subsequently, the attacker exploited the governance mechanism to endorse their own proposal, thereby enabling the transfer of funds to their designated wallet address. Following this, the funds extracted from the protocol were utilized to repay the flash loan.
Ranking second on the list, resulting in a substantial loss of $130 million, is Cream Finance, an Ethereum-based decentralized finance (DeFi) platform that fell victim to a hack on October 27, 2021. In this instance, the attack was not a straightforward flash loan exploit; instead, the hacker employed intricate strategies involving multiple deposits and withdrawals.
To elaborate, the hacker initiated a scheme wherein they borrowed $1.5 billion worth of Yearn protocol’s yUSD vault shares, using $2 billion in collateral. By contributing an equivalent amount of yUSD to the Yearn vault and doubling the share value, the hacker inflated Cream Finance’s debt to $3 billion against the $2 billion collateral. The resulting $1 billion surplus represented the hacker’s profit, although Cream Finance possessed only $130 million in asset value, effectively constituting the hacker’s ultimate illicit gain.
Fei Protocol, a DeFi platform on Arbitrum, experienced a breach on April 30, 2022, resulting in a loss exceeding $80 million. The attack encompassed a combination of reentrancy and flash loan exploits.
The security vulnerability of reentrancy was exploited, enabling the assailants to borrow assets while withdrawing all the provided collateral. Specifically, the attacker leveraged asset borrowing from the pool and utilized flash loans with numerous tokens/WETH as collateral. The borrow function within the contract lacked the check-effect-interaction pattern. This absence allowed the transfer of ETH to the attacker’s contract before updating the attacker’s borrowing records. These aforementioned steps were iterated for multiple tokens. Ultimately, the attacker repaid the flash loan and channeled the acquired profits through tornado cash for obfuscation.
How to prevent Flash Loan Attacks
- Smart Contract Audits: Conduct regular and thorough security audits of smart contracts to identify potential vulnerabilities that attackers might exploit.
- Flash Loan Fee Structures: Implement variable flash loan fees based on transaction sizes or introduce minimum collateral requirements to discourage large-scale flash loan exploits.
- Price Oracle Integration: Integrate reputable price oracles to provide accurate and real-time market data for DeFi platforms, reducing the impact of manipulated prices.
- Flash Loan Limits: Set transaction size limits for flash loans, reducing the potential magnitude of attacks and minimizing the risk of collateral liquidations.
- Enhanced Communication and Collaboration: Promote communication and information sharing between DeFi platforms to identify and mitigate interconnected flash loan attacks more effectively.
- Bug bounty platforms: Bug bounty programs can mobilize the crypto community to actively search for vulnerabilities. By offering rewards for discovering and reporting potential threats, projects can tap into the collective intelligence of the community.
Flash loan attacks pose a significant risk to the decentralized finance ecosystem, threatening the integrity and trust of DeFi platforms. By understanding the mechanics of these attacks and learning from past case studies, the DeFi community can take proactive steps to strengthen security measures and create a more resilient financial landscape, mitigating the potential impact of flash loan attacks.
Want to know more about a comprehensive approach to security and bug bounty programs? Get in touch to request a demo with our team today!

