During my recent bug-hunting session on HackenProof, I discovered a Critical severity issue that allowed me to dump users’ passports and IDs by running a simple brute-force attack with Burp Intruder.
The origin of this vulnerability lies in predictable file names and publicly accessible storage for files submitted for KYC verification. While I was investigating how the KYC functionality worked on that exchange, I noticed that files that I submitted to KYC, were uploaded to an external domain and automatically renamed to the 13 digits format, the first 5 or 6 digits were the same for each file, and the value of filename was incrementing for each file. At this point, such activity seemed strange to me, as I noticed a consistent pattern in it.
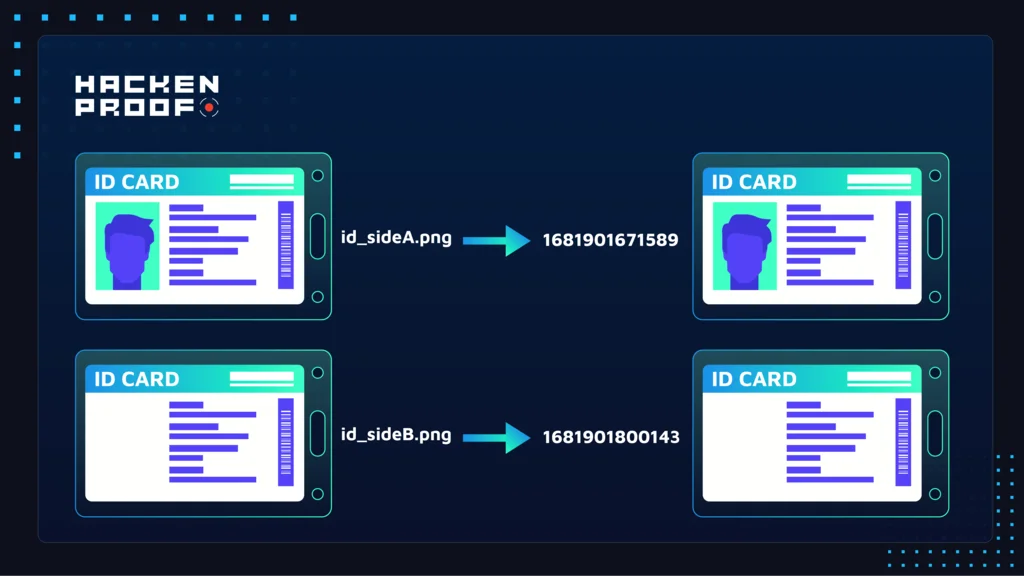
Further investigations helped me to discover that the filename pattern is a Unix timestamp converted in milliseconds. After that, I started a long-term brute force attack with Burp Intruder, and all I had to do then is wait until the valid filename will be found. The following screenshots demonstrate the exact attack I used for the exploitation of this vulnerability.
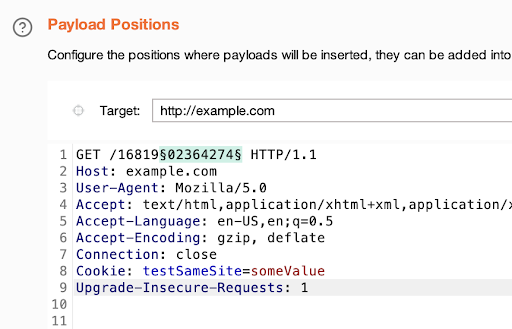
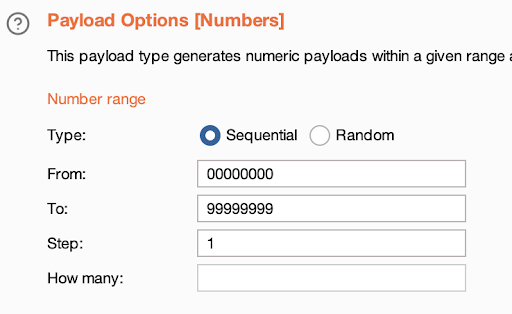
As a payload position, I’ve set several last digits of the filename, and a payload set consists of numbers that iterate one by one from the lowest to the highest value.
After several hundred thousand requests, I discovered a lot of IDs and passports of users who were actively submitting their documents for KYC verification.
As it was mentioned before, the core of this vulnerability lies in the predictable filenames and unrestricted access to the files. In case the filenames were truly unpredictable, like a hashed SHA256 string of its origin file name or etc, then the risk of this issue would be partly mitigated, as the prediction attack would be impossible.

