The cybersecurity landscape is more volatile than ever, with cyberattacks growing at a fast pace. In 2024 alone, cyberattacks surged by 75% compared to 2023, underscoring the urgent need for proactive security measures.
As cybercriminals continue to exploit vulnerabilities in digital infrastructures, businesses must prioritize robust security strategies to mitigate risks. The latest DeepSeek AI breach is a stark reminder of the consequences of inadequate security controls.
The Latest High-Profile Hack: DeepSeek AI
In January 2025, DeepSeek AI, a Chinese artificial intelligence startup, fell victim to a critical security lapse that exposed over a million sensitive log entries. The breach stemmed from a lack of authentication on a publicly accessible ClickHouse database, exposing chat histories, API keys, backend operational details, and metadata. The vulnerability has been identified by Wiz security team.
How Attackers Exploited the Vulnerability
The attack surface included open ports (8123 and 9000) on subdomains like oauth2callback.deepseek.com and dev.deepseek.com, leading directly to the unprotected database. Without authentication mechanisms in place, the database allowed unauthorized SQL query execution, exposing sensitive data and leaving DeepSeek’s infrastructure vulnerable to privilege escalation attacks.
Hackers could easily discover these exposed ports using basic network scanning techniques. With unrestricted access to the database’s HTTP interface, attackers could retrieve confidential data and manipulate records, leading to significant security and privacy risks.
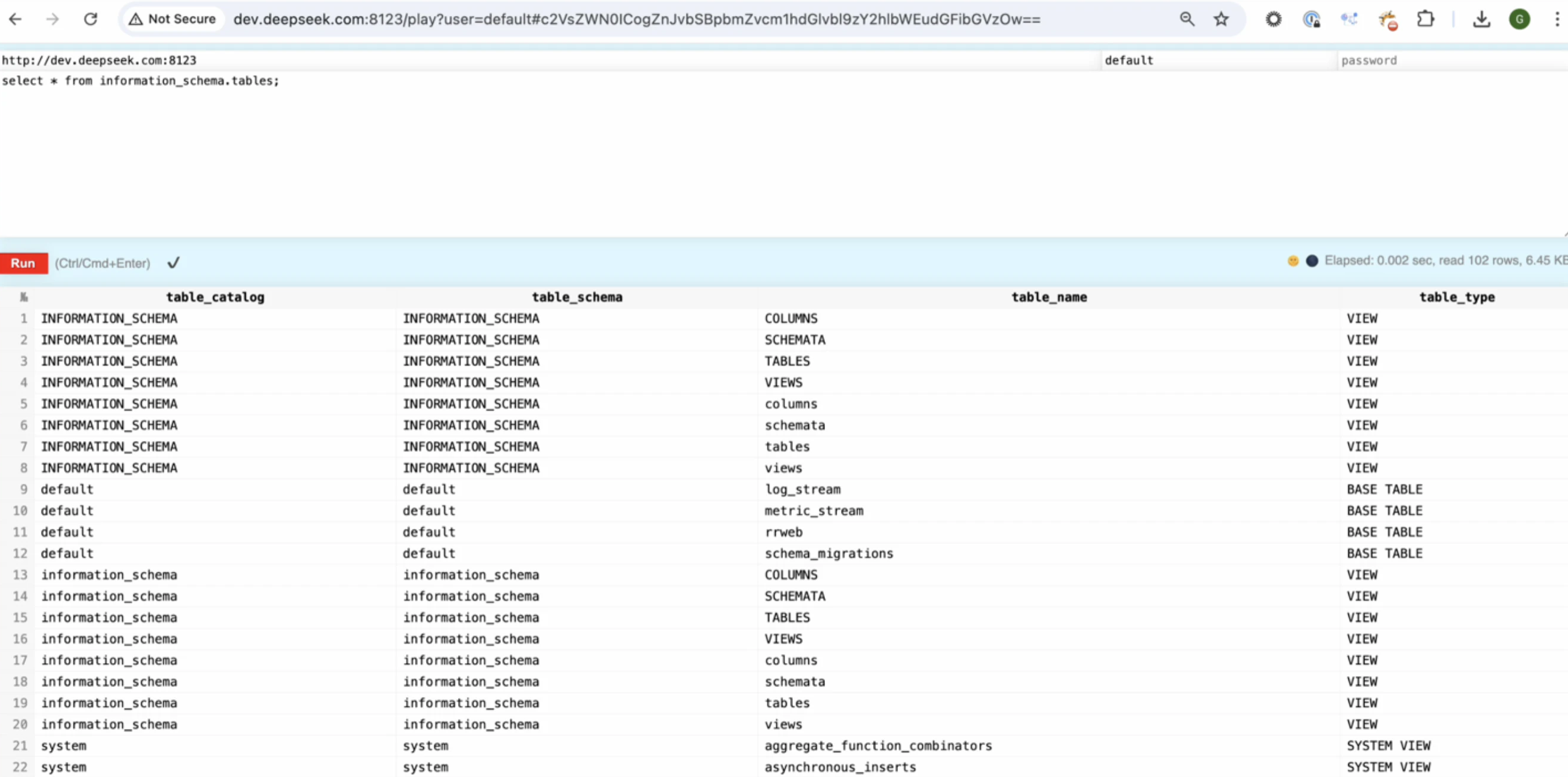
Impact of the Breach
The data exposure posed multiple threats, including:
- Unauthorized access to AI chat histories, compromising user privacy.
- Exposure of API keys and secret tokens, which could enable unauthorized access to other integrated services.
- Leaks of internal backend details, potentially allowing attackers to exploit further weaknesses within DeepSeek’s infrastructure.
This breach highlights the dangers of misconfigured cloud-based databases and reinforces the need for stringent security protocols.
Could This Attack Have Been Prevented?
A holistic security approach could have significantly reduced the risk of such a breach. The following key measures are essential in preventing similar attacks:
1. Security Audits
Regular security audits help identify misconfigurations and vulnerabilities before they can be exploited. Conducting periodic assessments ensures that security controls remain effective.
2. Penetration Testing
Simulated cyberattacks through penetration testing allow organizations to discover weak points in their infrastructure and remediate them before real attackers can exploit them.
3. Bug Bounty Programs
Engaging with ethical hackers through bug bounty programs provides a crowdsourced security approach to uncover vulnerabilities that internal teams might overlook.
A layered security strategy, combining these measures, is crucial in fortifying digital assets against emerging threats.
HackenProof’s Security Approach
At HackenProof, we specialize in Web3 security and proactive threat mitigation. Our crowdsourced security model leverages the expertise of over 40,000 professional ethical hackers to identify and address security weaknesses before malicious actors can exploit them.
By integrating security audits, penetration testing, and bug bounty programs, we provide a comprehensive defense strategy that aligns with industry best practices. Organizations that adopt this approach can significantly enhance their security posture and prevent costly breaches like the one experienced by DeepSeek AI.
Want to know more about bug bounty programs? Get in touch to request a demo with our team today!

