What is Slither
Slither is a Solidity static analysis framework based on Python 3. It is one of the most popular tools for smart contracts auditing. Slither has a wide range of vulnerability detectors, printers for visualization of the contract details, and API for custom analyses. It supports Solidity 0.4+ contracts and the audit time is fewer than 1 second per contract.
How to install Slither
Begin with installing solc – Solidity compiler:
sudo apt install software-properties-common
sudo add-apt-repository ppa:ethereum/ethereum
sudo apt install solc
You should also install the solc-select. It is used for quick installation and switching between Solidity compiler versions.
Simply run pip3 install solc-select
After the solc and solc-select are installed with no errors, we can proceed to the Slither installation. It can be done in three ways:
Using Pip:
pip3 install slither-analyzer
Using GitHub:
git clone <https://github.com/crytic/slither.git> && cd slither
python3 setup.py install
Using Docker
docker pull trailofbits/eth-security-toolbox
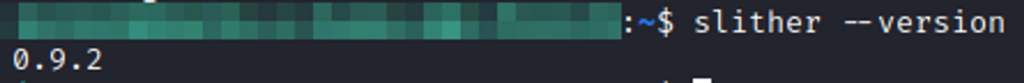
We can check the installation by running slither - -version in your terminal. If the tool is installed properly, you’ll see the latest version – 0.9.2.
How to check a smart contract using Slither
After you defined a contract that you want to check, the easiest way is just to run slither [target]. The target can be specified in several ways:
- Local copy of a contract file. Example: slither SecureContract.sol
- Project directory. Example: slither /path/to/the/project/SecureProject
- Mainnet contract address. Example: slither 0xf34960d9d60be18cC1D5Afc1A6F012A723a28811
Slither supports 15 networks:
- Ethereum
- Optim
- Ropsten
- Kovan
- Rinkeby
- Goerli
- Tobalaba
- BSC
- BSC Testnet
- Arbi
- Arbi Testnet
- Poly
- Mumbai
- Avax
- Avax testnet
- FTM
Let’s explore a smart contract that’s vulnerable to re-entrancy attacks. The tutorial contracts can be found in this GitHub repo.
The easiest way to scan the local copy of a smart contract is to run slither with a contract name. Within seconds you will receive the results:
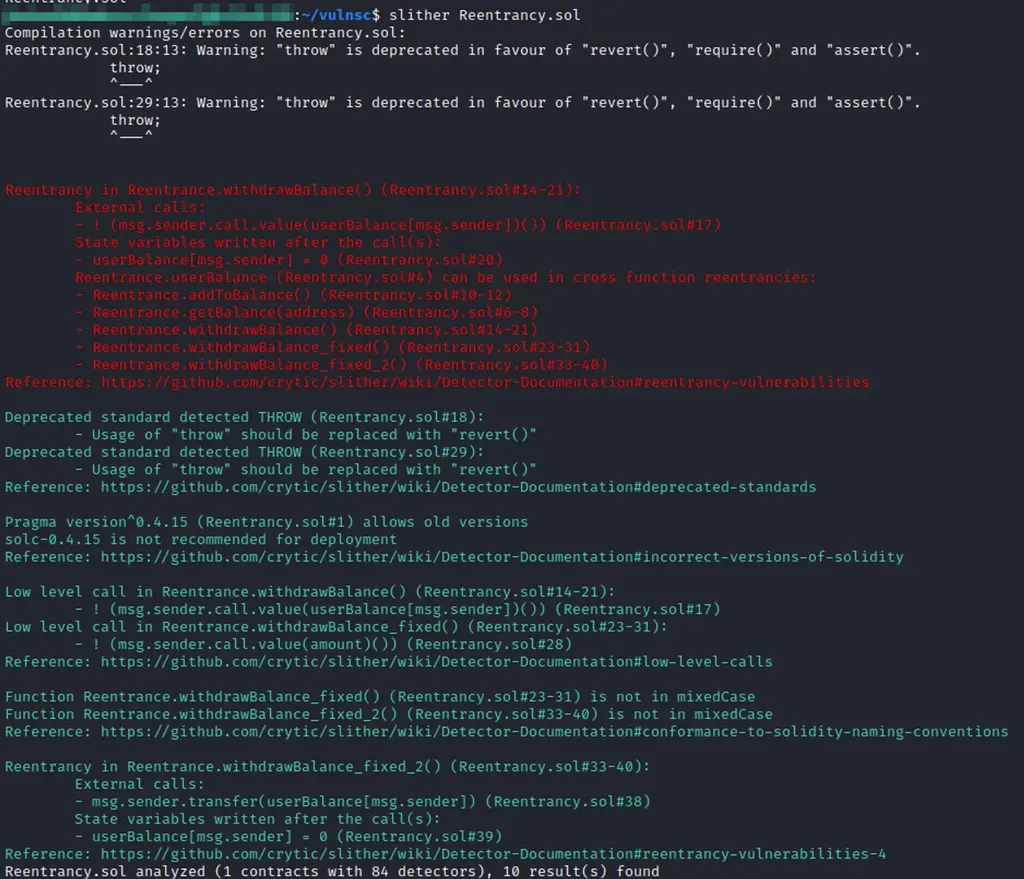
The colorized output highlights the most valuable audit findings. Slither also provides a detailed description of the vulnerability:
- how it works
- which functions are in use
- useful references
How to filter Slither output results
The output results can be filtered. Here are some examples how to filter the results:
dependencies: –exclude-dependencies
optimization: –exclude-optimization
informational: –exclude-informational
low findings: –exclude-low
Technically, you can even exclude medium and high-impact issues. But who’d be really interested in it?
How to use detectors in Slither
Detectors are used when you search for a specific type of vulnerability. There are 83 vulnerability detectors. You can find a full list of the detectors in this GitHub repo or by typing slither -h. To use a detector of your choice, run slither –detect [detector_name].
How to use printers in Slither
Instead of automatic analysis, printers can help you quickly extract crucial contract information. This may be helpful in manual analysis, audit reports, etc.
You can check the full list of the available printers by running slither –list-printers.
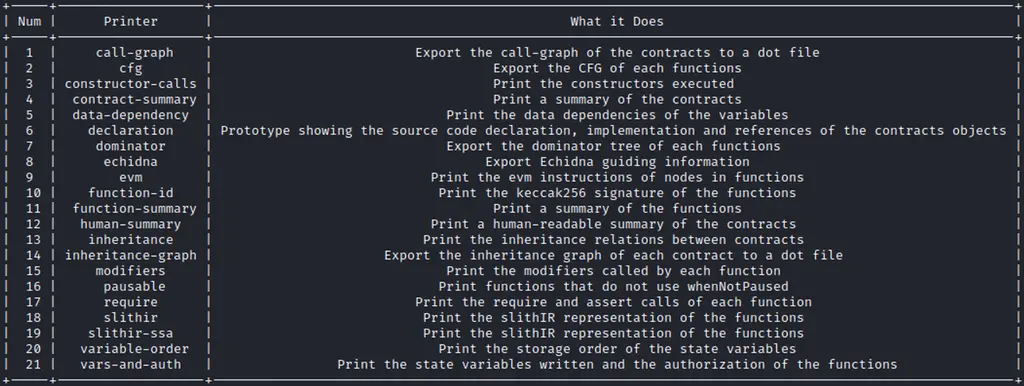
Here are a few examples of printers’ usage:
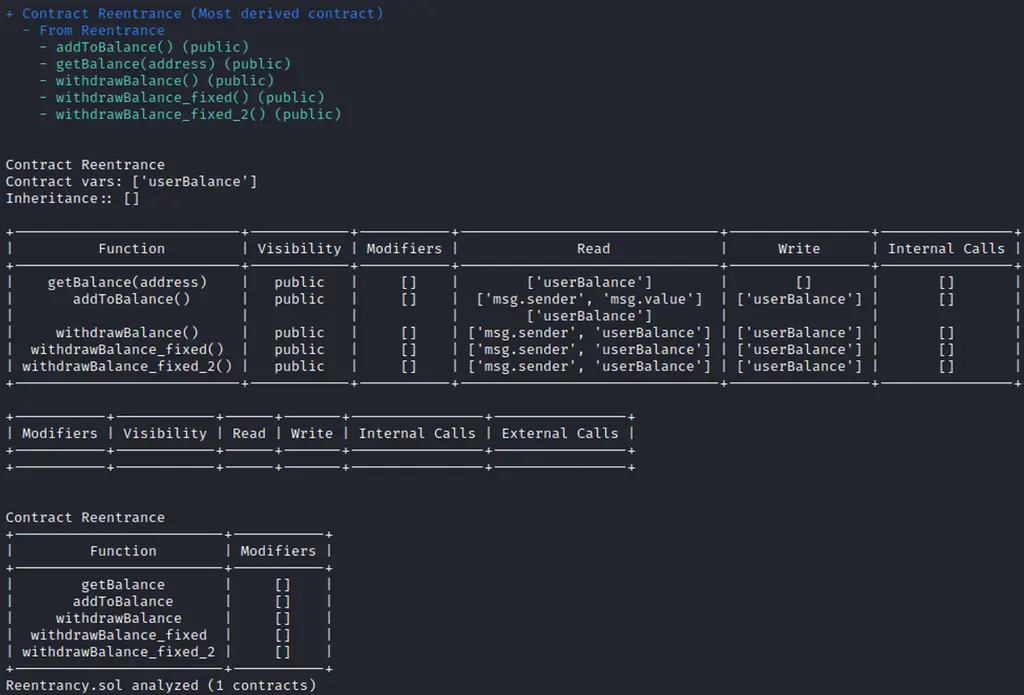
Running slither SecureContract.sol –print contract-summary, function-summary, modifiers will give us information about each function of the contract, its visibility, modifiers, internal and external calls.
Also, there’s a printer to build graphs to visualize the functions interactions inside the contract. Just run slither SecureContract.sol –print call-graph and the tool will generate a dot file that can be opened with any online dot viewer. Here’s an example of the mentioned graphs:
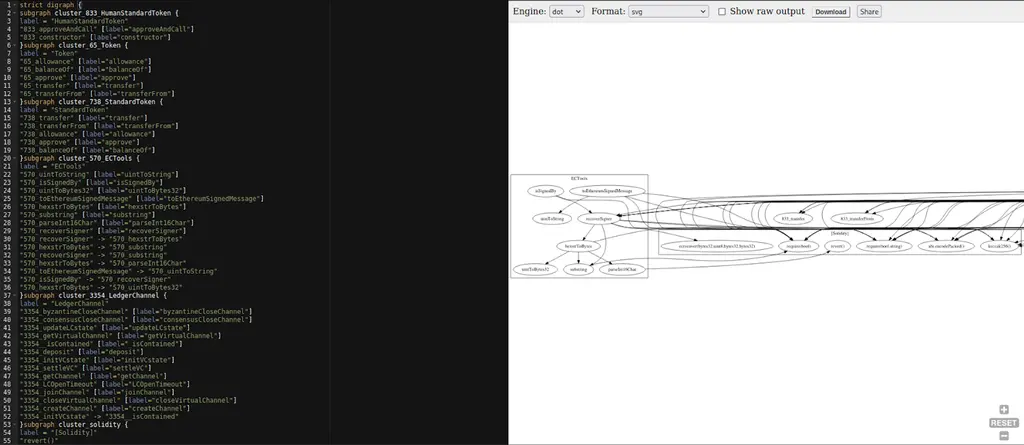
That’s it! Now we can run some basic checks of the smart contract, scan for the most popular vulnerabilities and extract important information for manual audits. You can try your new skills on our public smart contract programs to find valid bugs with a high bounty for them. But keep in mind that reports without a detailed Proof of Concept are out of scope, so do not forget to attach the PoC to your report.

