Intro
Pandora is a next-gen decentralized ecosystem that aims to redefine and disrupt decentralized finance through AMM, NFTs, and GameFi. Pandora is the first gamified DEX on the BNB Chain. Its ecosystem operates by means of a robust dual-token system and features cross-platform AMM, income-generating NFTs, P2P marketplaces, decentralized jackpot system, launchpad, fixed-interest securities, and much more.
Security issue overview
In cooperation with Pandora and HackenProof Bug Bounty platfrom, was fixed a security issue which could lead to stealing to drain the entire funds being used to pay fixed interest to NFT Security holders by calling the functionality BondRouter:harvest with crafted parameters only with having a valid NFT Security.
Anonymous bug hunter discovered a security issue, which was successfully validated and fixed. User funds were not affected.
To exploit this vulnerability, the attacker must have a valid NFT Security, then he can call the harvest function on the BondRouter with an array of identical NFT Security IDs, containing his own NFT Security ID.
The `executeHarvest` function should calculate the interest amount first and update the `lastHarvest` time of the NFT Security out of the for loop, meaning that the attacker could reuse his NFT Security ID and increase the interest amount which will be sent to him via the payment function.
Validation steps
Fot successfully exploitation the attacker should
- Mint a new BondNFT on Pandora NFT Security (https://invest.pandora.digital/)
- Wait for the correct time when the rewards are available and ready to be claimed
- Call the BondRouter: harvest function by supplying a special crafted payload on the info parameter
- A ClaimInfo array object containing the following things:
- A valid batchId
- An array containing its own NFT Security ID multiples times, for example: [1,1,1,1,1,1,1,1,1,1,1,1,1]
- When the function finishes its execution, the funds will be stolen by supplying just one NFT Security.
PoC:
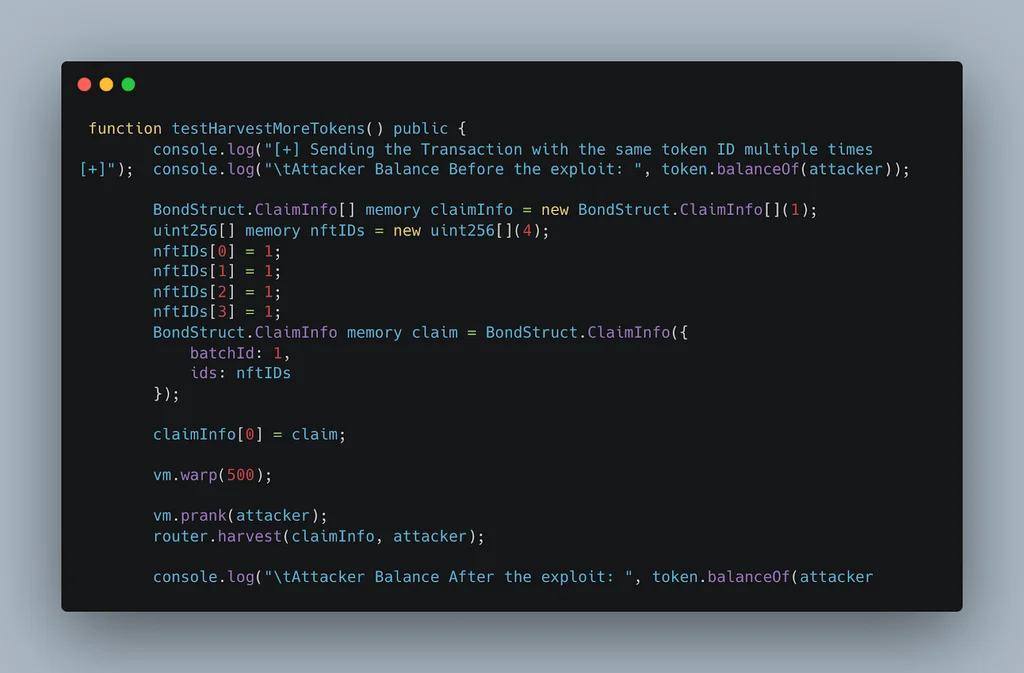
Vulnerability fix
The issue arise here, because `_updateLastHarvest` function is called once after all iterations of the loop
Before the fix:
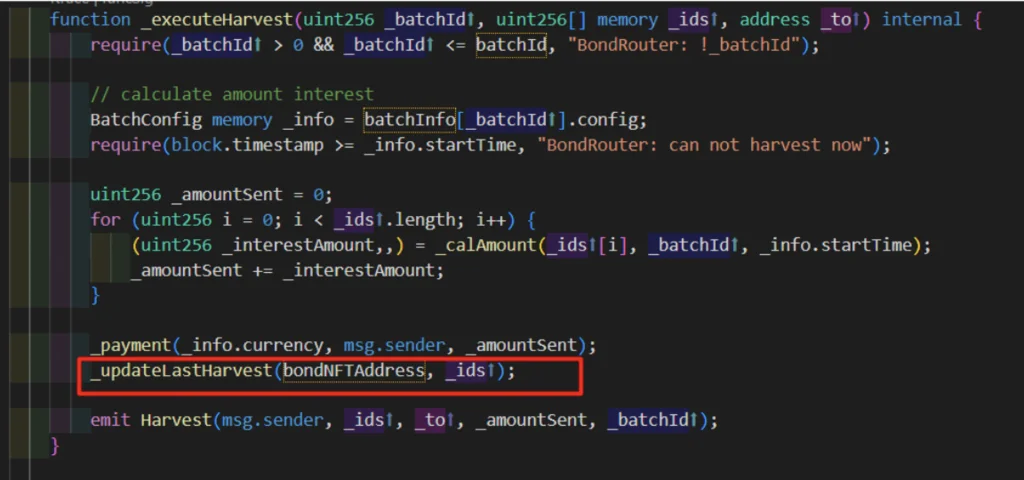
After:
So for the successful fix, the `_updateLastHarvest` function should be called after every iteration of the loop.
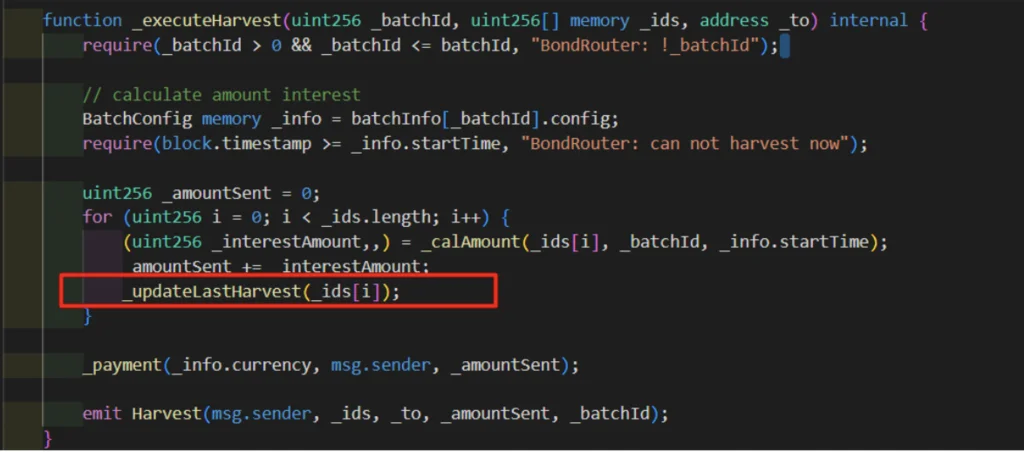
In the first code block, it is called after all of the interest amounts have been calculated and added up, whereas, in the second code block, it is called after each individual interest amount has been calculated. This would have an impact on the behavior of the code, as the timing of the _updateLastHarvest function would affect the state of the smart contract.
Conclusion
After the Pandora team has been notified of this vulnerability and resolved it in a timely manner, NFT Securities continue to impose no further risks to users and maintain their title as one of the most secure yet profitable investments that Pandora has to offer.
We would like to thank the anonymous whitehat for doing an amazing job and responsibly disclosing such an important bug. Also, we want to say thank you for the Pandora team for fast investigation of it.
Don’t hesistate to follow us on twitter/linkdin to read about more secuirty issue and bug bounty use cases.
Want to launch your bug bounty program? Message to…
Review all bug bounty programs available on HackenProof: https://hackenproof.com/programs and get up to $1 million bounty for valid issues.

