In this article, we will define what re-entrancy bugs are in the context of smart contracts, identify common scenarios that often lead to re-entrancy vulnerabilities and of course outline potential rewards and recognition for successfully identifying and reporting re-entrancy vulnerabilities.
We already witnessed 24 big hacks in the first half of 2023 with implementing re-entrancy technic and since the first introduction in 2016 (The DAO hack) this vulnerability cost users more than 100 mln.
A re-entrancy attack is a type of vulnerability, particularly in the context of blockchain and smart contracts, where an attacker takes advantage of the asynchronous nature of certain operations to repeatedly call a function before the previous invocation completes. This can lead to unexpected behavior, unauthorized access, and the potential theft of assets.
How Re-entrancy Attacks Work:

How Re-entrancy Attacks Work:
- Asynchronous Operations: In many systems, such as blockchain platforms like Ethereum, operations are often asynchronous. This means that when a function is called, it might take some time to complete, during which other operations can occur.
- State Changes and Shared Data: In the context of smart contracts, a key feature is the ability to change the state of the contract’s variables. However, if these state changes are not managed carefully, they can be exploited. Re-entrancy attacks typically target functions that involve state changes and interactions with other contracts or external systems.
- Vulnerable Function: The attack usually starts with a function in a smart contract that can be called externally. This function performs some critical actions, which might involve transferring assets (e.g., cryptocurrency tokens) to another contract or account.
- Attack Preparation: The attacker deploys a malicious contract or prepares a malicious function within their own contract. This function is designed to be called repeatedly in quick succession.
- First Invocation: The attacker initiates the attack by calling the vulnerable function in the target contract. Let’s assume this function involves transferring tokens from the target contract to another contract or account.
- Re-entrancy Exploit: Here’s where the magic (or rather, the vulnerability) happens. While the initial invocation of the vulnerable function is still processing, the attacker’s contract quickly calls back into the same vulnerable function.
- Repeating the Attack: At this point, the function’s state is not been updated yet to reflect the first invocation’s changes, and the contract’s logic might not have been completed. The attacker’s second invocation re-enters the function.
- Double Spending: The attacker’s malicious function can now execute actions using the context of the first invocation. This might involve transferring tokens again, effectively “double spending” them.
- Repeat and Amplify: The attacker can continue this process, repeatedly calling the vulnerable function and transferring tokens multiple times before the original invocation completes. This amplifies the impact of the attack.
The incident involving the dForce platform serves as a notable example of how vulnerabilities within decentralized finance (DeFi) protocols can be exploited (https://twitter.com/peckshield/status/1623902441992523776). The attack against the dForce protocol involved targeting the Curve Finance vault within the context of the Arbitrum and Optimism blockchains. The breach exploited a reentrancy vulnerability present in the code utilized for accessing price oracles when engaging with Curve on either Arbitrum or Optimism.
This specific type of reentrancy vulnerability, characterized by its read-only nature, is widely recognized. Similar attacks have been previously executed against Curve pools utilized by Midas Capital and Market.xyz. To capitalize on the vulnerability, the attacker introduced flashloaned funds into the system and subsequently withdrew their deposit. During this withdrawal process, the attacker leveraged the reentrancy vulnerability to manipulate the apparent virtual asset price.
Through the strategic reduction of the virtual price, the attacker orchestrated the liquidation of positions held by other users in the wstETH/ETH pool. This orchestrated liquidation resulted in the misappropriation of approximately $3.6 million from the dForce protocol.
Remarkably, this DeFi breach culminated positively. The dForce team formally requested the restitution of the funds, leading the attacker to return all pilfered assets to the project’s multi-signature wallets.
There are some examples of Soligity smart contracts:
1. Ether Transfer Reentrancy:

In this example, the ‘Attacker’ contract repeatedly calls the ‘withdraw’ function of the ‘Vulnerable’ contract, which transfers Ether to the attacker’s address. The attacker then uses a fallback function to call ‘withdraw’ again, creating a recursive call and allowing them to repeatedly drain the vulnerable contract’s balance.
Untrusted External Calls Reentrancy:
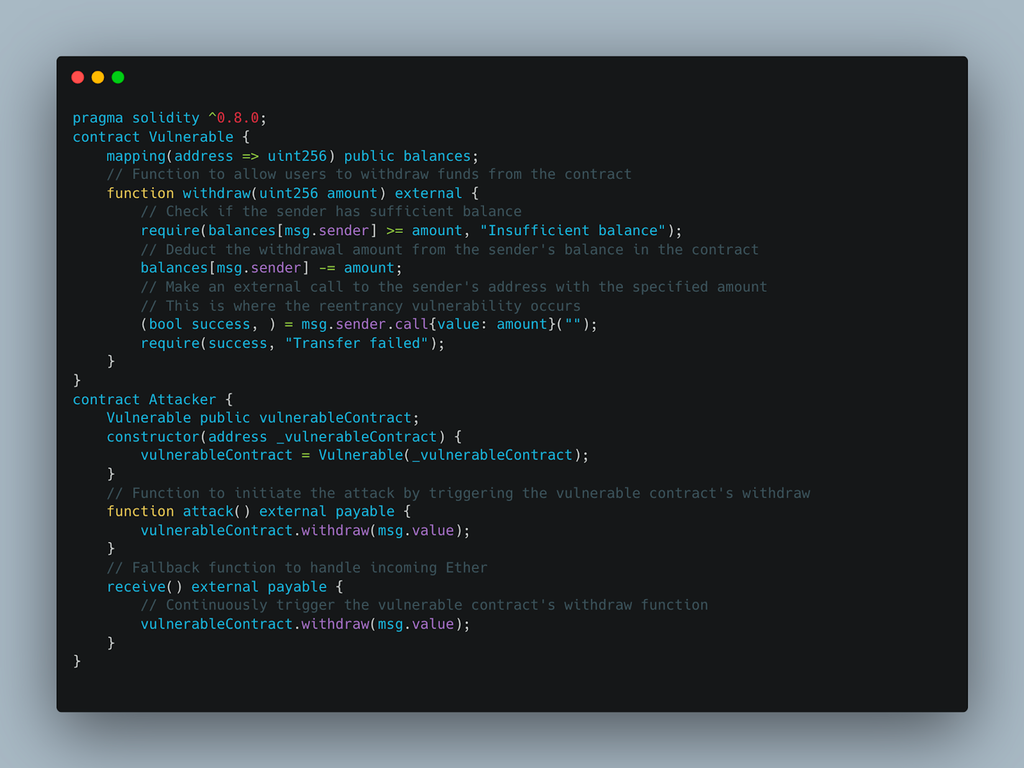
In this example, the ‘Vulnerable’ contract makes an external call to ‘msg.sender’ without properly handling the control flow. The ‘Attacker’ contract calls the ‘withdraw’ function with a large amount of Ether, causing the ‘Vulnerable’ contract to call the attacker’s contract, allowing for reentrancy attacks.
Callback Reentrancy:
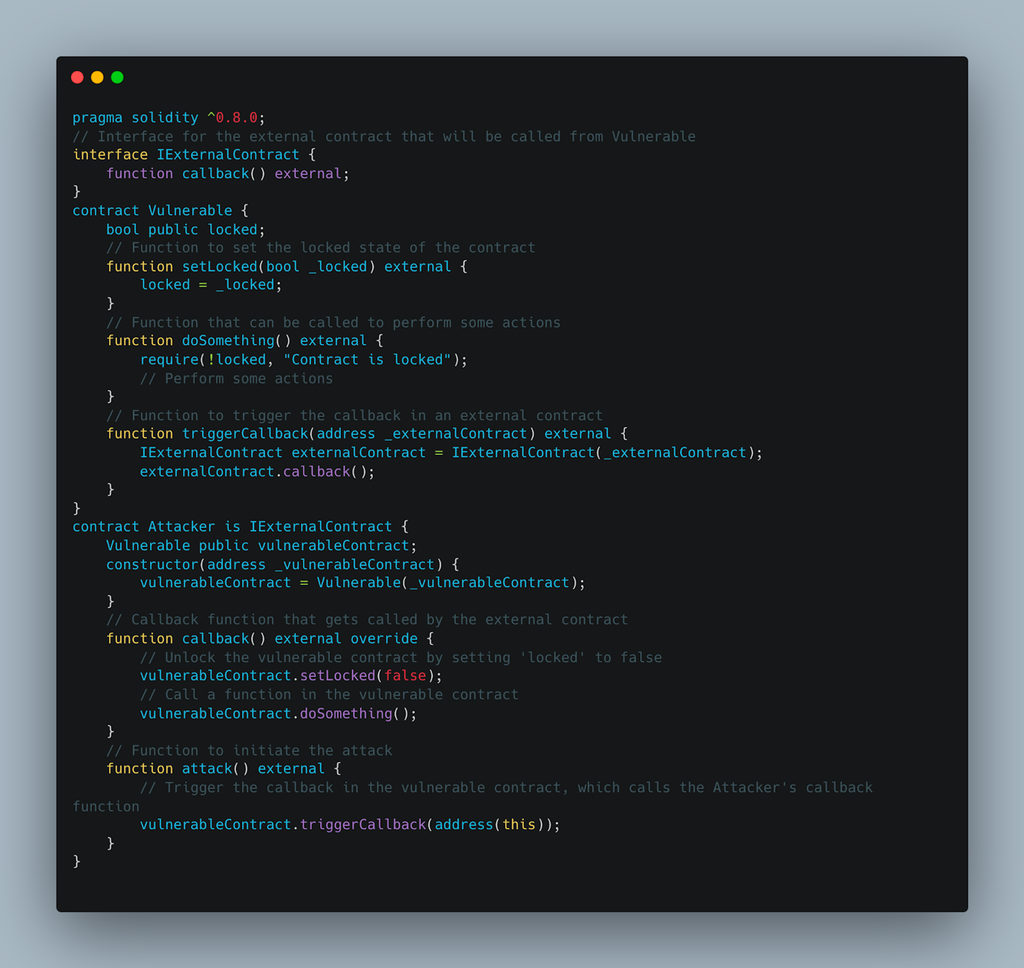
In this example, the ‘Vulnerable’ contract relies on an external contract’s callback function to execute some logic. The ‘Attacker’ contract implements the callback function and sets the ‘locked’ state of the ‘Vulnerable’ contract to false, allowing the attacker to call the ‘doSomething’ function and potentially disrupt the contract’s intended behavior.
A guide to detecting re-entrancy errors in blockchain smart contracts:
As an ethical hacker, it is your role to diligently identify vulnerabilities that could compromise the security of smart contracts on the blockchain. One of the most important areas of focus is identifying re-entrancy errors that can lead to serious exploits. Follow these instructions to effectively detect re-entry errors in smart contracts:
- Adopt the Checks – Effects – Interactions template: Start by using the Checks – Effects – Interactions template. This method takes a systematic approach: first check conditions, then initiate a state change, and finally interact with external contracts. By examining the delay between state changes and external interactions, you can diagnose a potential re-entrancy attack.
- Search for security enhancement modifiers: Consider modifiers in your assessment. In the context of smart contracts, Ethereum Solidity supports modifiers. Verify the correct application of modifiers that impose conditions before performing functions. This practice will help you find re-entry vulnerabilities created by not imposing the necessary restrictions before executing a function.
- Be careful with external calls: Focus on examining the vulnerabilities of critical functions that are exposed to external calls. Make sure that the contract you are reviewing has the ability to interact with these functions. This way, you can validate the likelihood of re-entrancy in through external interactions.
- Check the security of the withdrawal scheme: Determine whether secure withdrawal models are in place. If the withdrawal is realized by automatic transfers to external addresses, there is a high probability of a re-entrancy attack. Such an uncontrolled approach to withdrawals increases the likelihood of re-entrancy errors that may occur during the transfer.
- Consider testing implementing mutex control locks: In the absence of mutex locks, there will be no protection against multiple calls to the same function by the same user, especially before the previous call has completed.
- Always check gas limits: Lack of a strategically set gas limit when evaluating external calls. The absence of such a preventive measure may allow attackers to consume excessive amounts of gas per call, thereby increasing the potential impact of re-entrancy attacks.
By carefully following these instructions, you will be able to effectively detect re-entrancy errors in blockchain smart contracts. Your commitment to ethical hacking will go a long way toward improving the security and integrity of blockchain-based systems.
This article should give you a basic understanding of the problem of re-entrance attacks and how to find such vulnerabilities so now we welcome you to test your knowledge on our platform where you can find a lot of targets for your research!
And do not forget to subscribe to our social media and email newsletter to not miss out on news and coming-up articles.

