The Sui blockchain ecosystem has seen a surge in the number of projects taking root. As with any rapidly growing space, it’s vital to understand the security measures taken by these initiatives. This report delves into the security conditions of the Sui projects, categorized into dAPPs, infrastructure, and wallets.
Total Projects and Security Measures
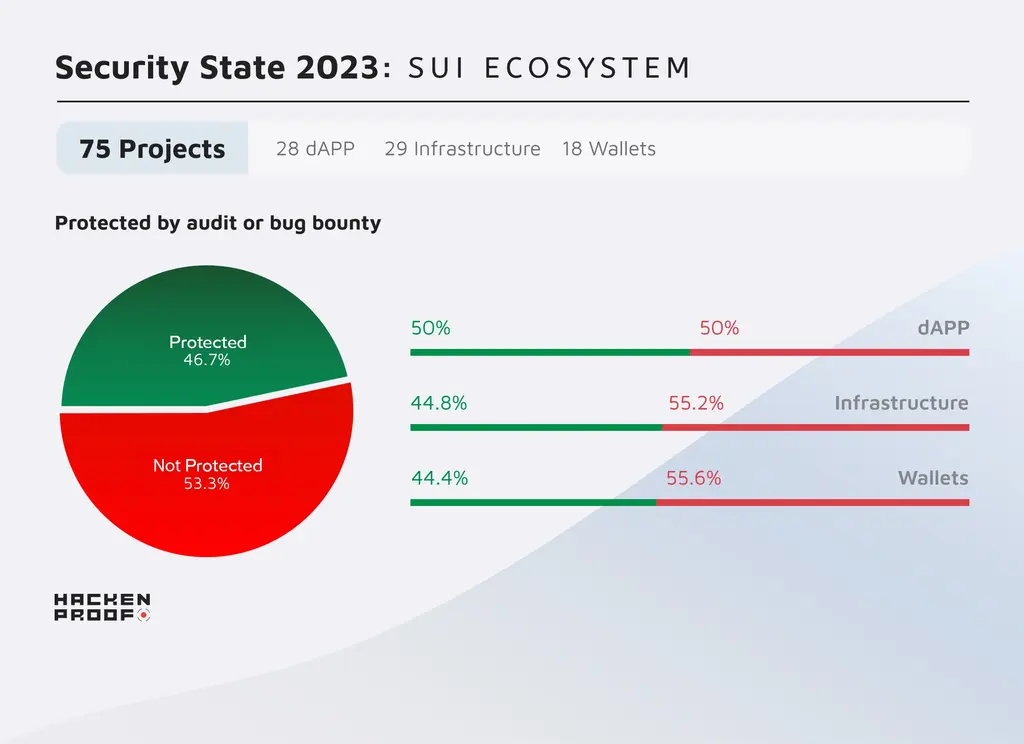
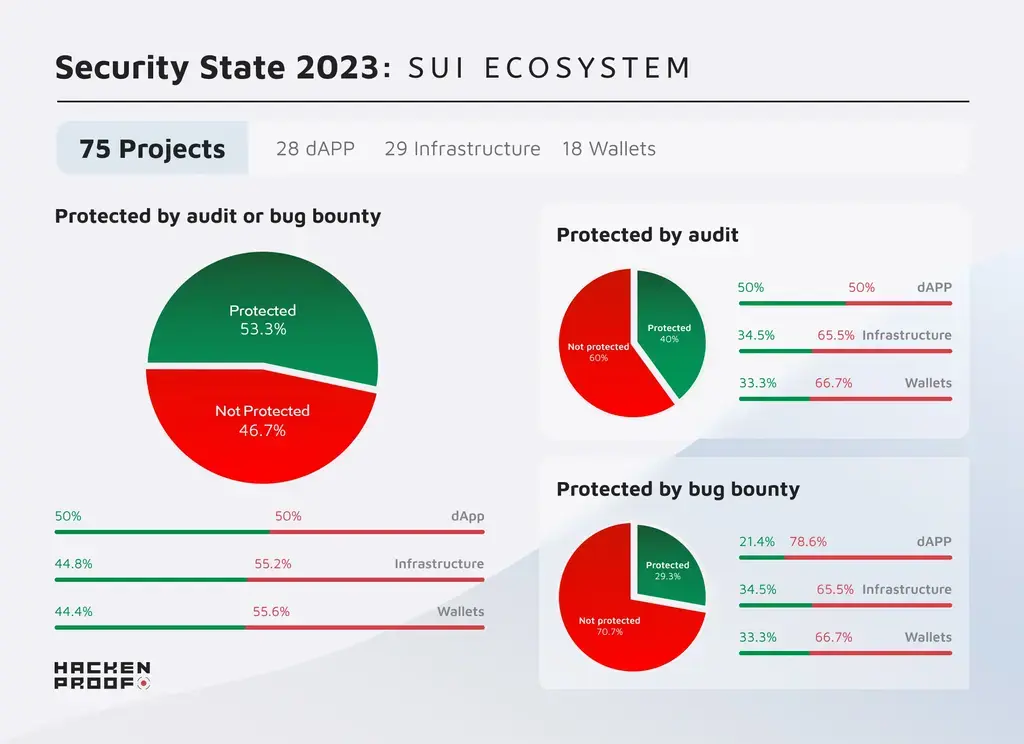
As of 2023, the Sui ecosystem boasts 75 projects. Of these, 35 have either undergone an audit or have established a bug bounty program to identify vulnerabilities. Unfortunately, this means 40 projects have not taken either of these crucial security steps.
Breakdown by Project Type
| Project Type | Total | Audited | Not Audited | With Bug Bounty | Without Bug Bounty |
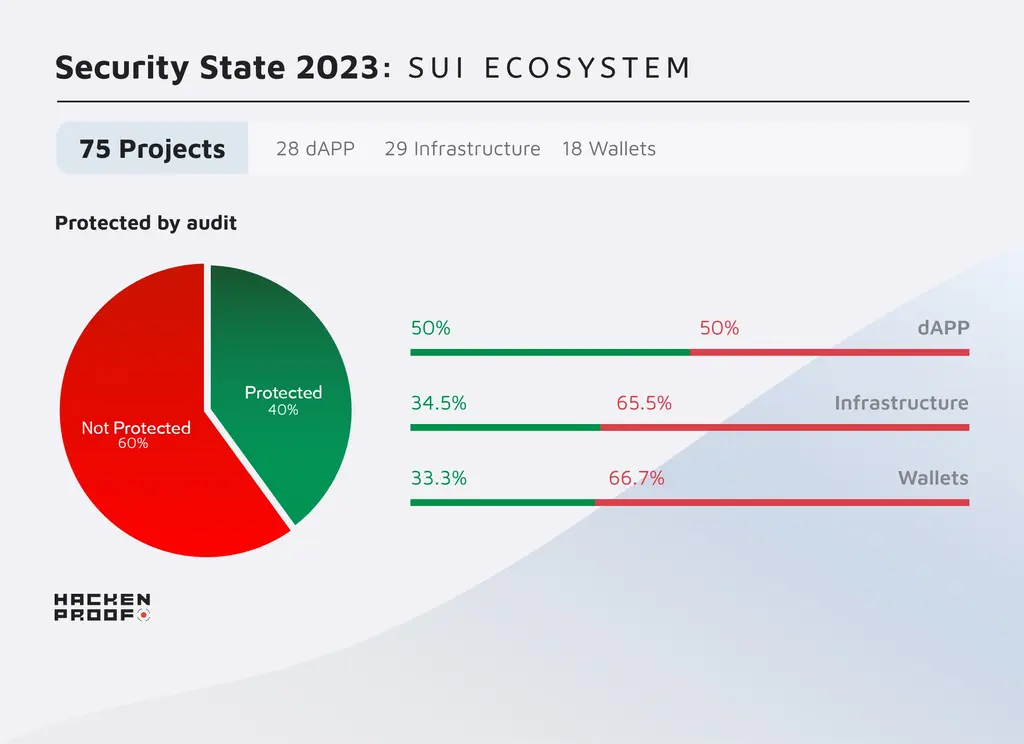
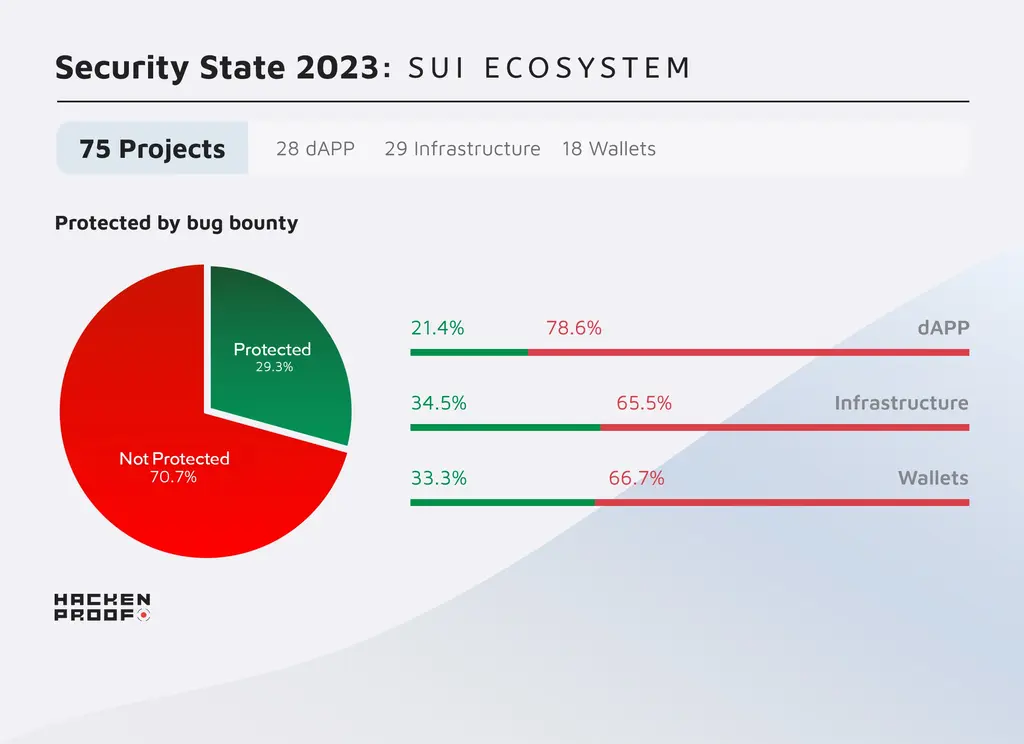
| dAPPs | 28 | 14 | 14 | 6 | 22 |
| Infrastructure | 29 | 10 | 19 | 10 | 19 |
| Wallets | 18 | 6 | 12 | 6 | 12 |
Conclusion
The data indicates that while a significant number of projects recognize the importance of security audits and bug bounties, there remains a sizable portion that has not yet adopted these practices. Especially in spaces such as infrastructure, which forms the backbone of the ecosystem, security should be a top priority.
The Sui protocol boasts robust security measures, with over 45% of its projects benefiting from third-party software audits and bug bounty programs. While this percentage is certainly impressive, it is important to note that many projects within the Sui ecosystem are open-source and leverage pre-tested and audited solutions that make this ecosystem safe and secure.
Nevertheless, Sui has consistently demonstrated its reliability and security as a protocol for both utilization and development. Furthermore, Sui stands out by offering scalability and low-latency capabilities, enabling parallel transaction processing. In addition, Sui supports the utilization of the powerful smart contract language known as Sui Move, empowering users to define and manage assets and associated operations with confidence.

