Intro
Ternoa is a blockchain technology company that specializes in secure digital transmission. Their technology utilizes a secured blockchain and decentralized storage providers to ensure the long-term integrity of encrypted and segmented data. This enables users to secure the data contained in NFTs using multi-party cryptography, facilitating safe and reliable digital asset transactions and data transfer. Ternoa’s approach combines confidential computing with decentralization, allowing users to encrypt data off-chain with on-chain access control of keys. This opens up a broad range of applications for their technology.
Summary
In January 2024, a vulnerability was responsibly reported by a security researcher who is also known as @rapt00r via Ternoa’s Bug Bounty Program on HackenProof. This security flaw, discovered within Ternoa’s Auction Pallet, allowed for the potential theft of NFTs listed on the marketplace without compensation to the rightful owners. The Ternoa team swiftly took action to rectify the flaw and deploy the fix on the mainnet network, ensuring the security of operations on their platform. This collaboration underscores the value of ethical hacking in strengthening blockchain security.
Ternoa team has further confirmed that this vulnerability has not resulted in loss to any user on any marketplace on the mainnet. One of the main reasons is the high economic cost to execute such an attack and loss of reputation for the marketplace among the community.
Vulnerability Analysis
In the Ternoa blockchain, a security vulnerability was identified within the Auction Pallet, a crucial component responsible for the facilitation of NFT sales. The vulnerability stems from the system’s failure to permanently record the commission_fee at the inception of an auction for an NFT. This oversight leads to the fee being recalculated during the final payment process. During the payfornft function, where various computations take place, including the deduction of commission fees from the seller’s proceeds and the calculation of the creator’s fees, the mutable nature of the commission_fee permits a market owner to adjust it to the full sale price of the NFT. Consequently, this results in the full payment amount being erroneously directed to the market owner instead of the rightful NFT owner and creator, with the market owner also acquiring the NFT itself.
List of parameters currently taken while creating NFT Auction:
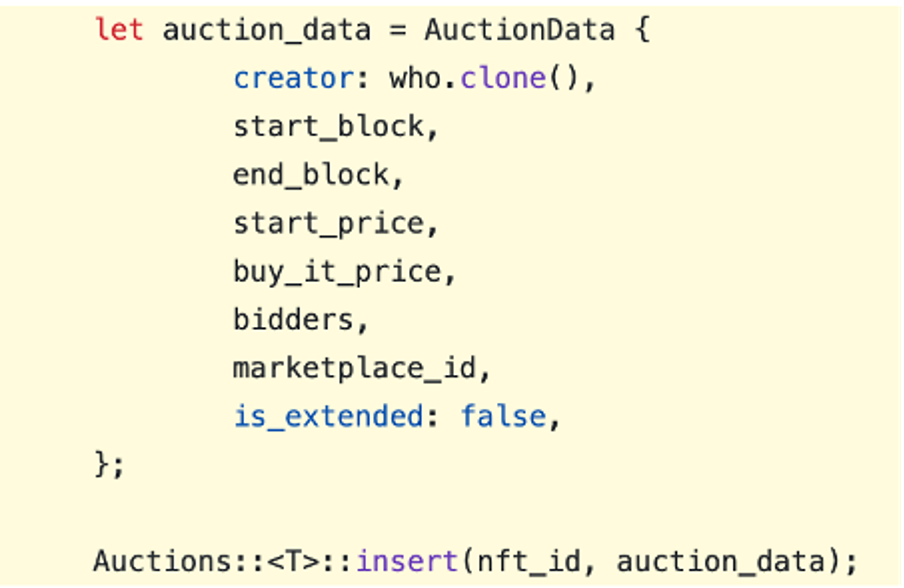
As you can see, the commission value is not set while creating an auction. The severity of this bug lies in its potential to defraud legitimate NFT owners and erode trust in the platform. The prescribed resolution is a code update to ensure commission fees are immutably stored upon listing, nullifying any subsequent tampering attempts by marketplace owners.
Proof of Concept
An attacker strategically establishes a marketplace, enticing users with notably low transaction fees. In this environment, a user then lists a highly valuable NFT for a “buy now” price of 100,000 tokens. Observing this, the attacker initiates a scheme to acquire the NFT at no cost. By altering the commission_fee to equal the NFT’s listed price, the attacker is poised to engage the “buy it now” feature. This deceptive move ensures that upon completion of the transaction, the manipulated commission fee is funneled back to the attacker, along with ownership of the NFT. The original owner, expecting legitimate remuneration, receives nothing, as the tokens exchanged for the NFT surreptitiously return to the attacker’s account.
Remediation
To rectify the vulnerability, it is essential to implement a fix in the Marketplace Pallet whereby the commission_fee is captured and locked in the Sale object at the exact moment an NFT is listed. This method ensures that even if a marketplace owner attempts to modify the commission_fee after the NFT has been listed, the stored fee will remain constant, safeguarding against manipulation and preserving the integrity of the transaction.
Acknowledgments
We extend our heartfelt gratitude to the security researcher for their meticulous and responsible disclosure of the vulnerability. This highlights the crucial role of public bug bounty programs and the significant contributions independent researchers make to the advancement of the industry. Our thanks also to the Ternoa team for their prompt response, active engagement, and the generous bounty provided.

